Disclaimer: this article includes links to products for sale on our store.
In this post we are going to cover:

Plus more... Read on to learn everything you need to know about SIM Swapping.
Did you know that your cellphone can offer a way for fraudsters and cybercriminals to access your personal information and financial accounts?
Yes, a scam called SIM swapping is a thing and it allows scammers to use your mobile number to take over your financial accounts.
SIM swapping use phone-based authentication to do this. For a successful SIM swap scam to take place, cybercriminals hijack your mobile phone number and use it to reach your sensitive personal information and bank accounts.
Here’s the short version of how it works. You might attempt access to one of your bank accounts that uses text-based two-factor authentication. This refers to when you start to access your account by typing in your user name and password.
Then your bank sends a code to your mobile device for you to continue the login process.
But some scammers can change the SIM card linked to your mobile number. That offers them control over the phone number, meaning they can receive access to your bank account and your finances.
We’re here to tell you all about SIM card swapping and how to protect yourself against this kind of scam. Here’s everything you must know.
What Does a SIM Swapping Attack Involve?
A SIM swapping attack is otherwise known as SIM splitting, SIMjacking, SIM hijacking, and port-out scamming. It’s a scam that happens when fraudsters use the weakness of two-factor authentication and verification which involves the second step of the process receiving a text message or phone call to your cellphone number.
Let’s say I have a Coinbase account and I have it set up to require a password and a one-time code generated by Authy, but my Gmail account tied to that Coinbase account doesn’t use Authy and just uses SMS for two-factor. Once I SIM swap that person, I can often also use that access to [request a link via text message] to reset his Gmail password, and then set up Authy on the Gmail account using my device. Now I have access to your Coinbase account and can effectively lock you out of both.
Let’s go over some of the basics of SIM cards. SIM cards are used as storage for people’s data in Global System for Mobile (GSM) phones.
If you haven’t got a SIM card in a GSM phone, it’s unable to use a mobile network. That means having access to your mobile number is extremely useful for scammers.
But the main question is – how do fraudsters gain access to your phone number?

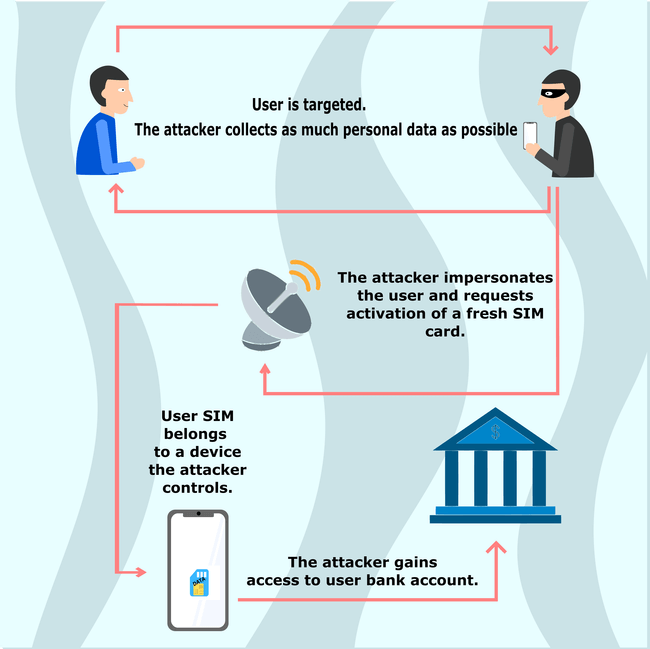
Cybercriminals begin by collecting as much personal data on you as possible. They gather information on you by sending phishing emails, using malware, researching you via social media, and utilizing the dark web.
When scammers have enough data, they speak to your mobile carrier. They impersonate you and pretend to have lost or damaged (your) SIM card.
Fraudsters will then request the activation of a fresh SIM card for their possession. If the scam is successful, this ports your cell number to the scammer’s mobile with a different SIM.
Alternatively, fraudsters may pretend that they need assistance switching to a new mobile device.
Once they can control your mobile number, scammers can then use your phone number to gain access to your bank accounts and other organizations. As many banks use access codes sent to mobile devices for entry, scammers can receive any codes or password resets straight to their device.

Once they’ve gained access to your bank account, they may set up a second account in your name at the bank. As you’re already a customer, there may be less vigorous security checks. Then, they can go ahead and make transfers between the two accounts without raising the alarms.
How Can a SIM Swapping Attack Be Prevented?
Thankfully, there are many ways you can help protect yourself from SIM swapping scams. Here’s how to protect against SIM swapping frauds.
Be Aware of Email Phishing

One way to prevent SIM swapping is to learn how to protect yourself against phishing emails. That way you can stop scammers gaining access to personal data that can help them persuade your bank or mobile phone provider that they are you.
Advice: Learn how to recognize and avoid phishing scams here. You can also discover how to keep your personal information safe and secure online here.
Update Your Account Security

Another idea is to improve your mobile device’s account security. Opt for a strong password that would be almost impossible to guess and use questions and answers that only you know the answers to.
Add Another PIN Code
![]()
If your mobile carrier lets you choose a different passcode or PIN for your communications, it’s a good idea to do so for an extra dose of protection.
Select Companies That Use Call-Backs

Many companies call customers back to ensure they’re speaking to the correct person before offering access to accounts. This is an effective way to keep accounts safe and to catch out identity thieves.
Use a Hardware Authentication Device like Yubikey

If you want to step up your two-factor authentication even further, you can choose a physical hardware device like a Yubikey.
These small fobs fit on your keyring and plug into your computer’s USB port to help confirm your identity. If you’re using a physical device like a Yubikey as well as your password and turning off SMS, then a scammer will literally have to steal your keys to gain access to your phone number. That makes it very unlikely for a SIM swapping scam to take place.
Avoid Using Authentication Apps as well

Authentication apps like Google authenticator and Lastpass authenticator are certainly more secure than SMS two factor. They use temporary passcodes generated by a service server and are shown only on your local device. However, even these apps suffer from security holes and poor user experience that make them confusing. While its better than SMS, we still recommend you forgo authenticator apps as soon as your hardware two factor (such as your Yubikey) arrives in the mail and you can get it set up.
Pros
- Authentication apps are more secure than SMS two factor
- The temporary passcodes generated are shown only on your local device
Cons
- Security holes
- Poor user experience
- Not as secure as hardware two factor
Pros
Cons
- Authentication apps are more secure than SMS two factor
- Security holes
- The temporary passcodes generated are shown only on your local device
- Poor user experience
- Not as secure as hardware two factor
Info: The short story is: stop using apps like google authenticator sooner rather than later.
Conclusion
SIM swapping scams are one big reason why relying on a cellphone number isn’t the best method of confirming your identity to organizations like banks. By investing your time into extra layers of protection, you can keep your personal information, bank accounts, and identity safer. Discover more information on how to protect your phone and the data on it here.
FAQ
What is SIM Swapping?
SIM Swapping is a fraud that exploits the mobile service providers feature to port a telephone number to another device with a different SIM.
How to protect yourself from SIM Swapping?
Keep your personal information safe and secure online, add strong passwords in combination with security questions, call your mobile carrier and ask them how can you protect your account by adding a PIN or password, and use a hardware authentication device like a yubikey.
How to tell if you've been SIM Swapped?
The first sign of a SIM Swapping attack is that the SIM card loses all service, and won’t be able to receive calls, texts, or access the internet.
What to do when SIM Swapping happens to you?
Call your mobile carrier and let them know that you didn’t make any changes to your SIM or account. You should also get in touch with your bank and check for transactions that aren’t yours.



