Disclaimer: this article includes links to products for sale on our store.
- Introduction
- Bitcoin Wallet Security
- What About Software Wallets?
- Backing Up the Wallet
- The Best Wallet Backup Method (Recommended)
- FAQ
In this post we are going to cover:

Plus more... Read on to learn everything you need to know about how to backup a Bitcoin wallet.
Did you just get your first Bitcoin?
Wondering about the best way to back it up?
Introduction
Times are changing as a country’s standard currency isn’t the only game in town.

Cryptocurrency first emerged in 2009 with the release of Bitcoin. Ever since, Bitcoin has risen in value, leading to the creation of other cryptocurrencies.
Naturally as the value of these currencies increases, the need for security will as well.

However, this security can be somewhat tricky to achieve due to the nature of cryptocurrency.
With cryptocurrency existing in areas all over the world, users must back up their Bitcoin currency in case of the following:
- Wallet theft
- Wallet damage
- The classic “lost my wallet” situation.
Bitcoin Wallet Security
Hardware Wallets

Hardware wallets are the preferred option over software wallets for cryptocurrency users to backup their information in a secure manner.
Why Are Hardware Wallets More Secure?
Since hardware wallets are physical devices, users are required to press buttons on the device to confirm transactions manually.

Manual input requirements make hardware wallets more challenging to hack, which leads to users storing more significant amounts of currency on the device. Manual input requirements include the following:
- Pin codes that must be entered in person
- Distinct backup phrases that are used to recover private keys from a lost, stolen, or broken wallet
Info: An additional line of defense that hardware Bitcoin wallets have is offline storage. Offline storage could make it, so your device is never exposed to the outside world. You're going to have to spend some money when purchasing a hardware wallet. While you might be hesitant, it's worth it to pay a little extra to protect your cryptocurrency that might otherwise be vulnerable.
Potential Disadvantages of Using a Hardware Wallet
- While hardware wallets offer recovery phrases, you still need to keep track of the small, physical item
- If you write down your recovery phrases on a piece of paper, you can lose the paper, or have the paper be compromised by weather elements such as fires and floods
- Hardware wallets can be a bit more difficult for users to navigate compared to software wallets
COMPARISON
What About Software Wallets?
Software wallets consist of storing cryptocurrency on programs or apps that can be accessed via a smartphone or computer.
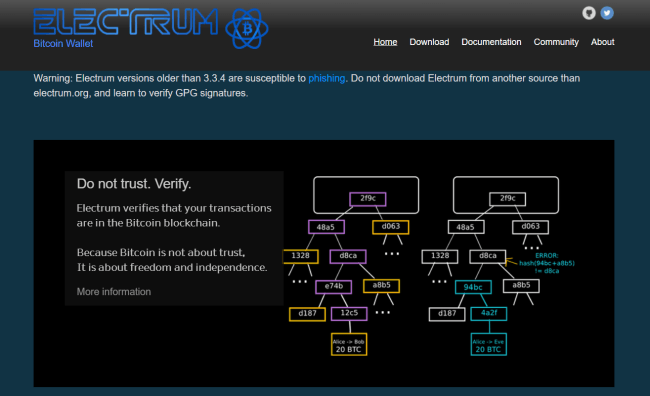
While software wallets are more straightforward than operating a hardware wallet, the level of security is lower, which increases the risk of the device being compromised.
Info: Reduced security leads cryptocurrency users to utilize software wallets for smaller transactions. Hot wallets are a typical example of a software wallet that stores lesser amounts of Bitcoin.
What Backing Up a Bitcoin Wallet Does
Backing up a Bitcoin wallet serves to store the user’s private keys and public addresses under a recoverable file in case your wallet gets stolen, damaged, or lost. Computer or software failure is an additional reason as to why you should back up your Bitcoin wallet.
Advice: It is recommended that you backup a Bitcoin wallet as an accessory to other Bitcoin wallets instead of storing all your currency in one device.
Private keys are essential as they distinguish who owns the Bitcoin, which allows users to send Bitcoin. Public addresses act in contrary fashion as they enable users to receive Bitcoin.
Warning: Backup is essential. If you lose your backup data and can't access your wallet, your bitcoins are permanently gone.
Backing Up the Wallet
Storing the Seed Words (AKA Recovery Phrase)
Billfodl acts as the ultimate tool for Bitcoin users to safely store their sensitive cryptocurrency info.
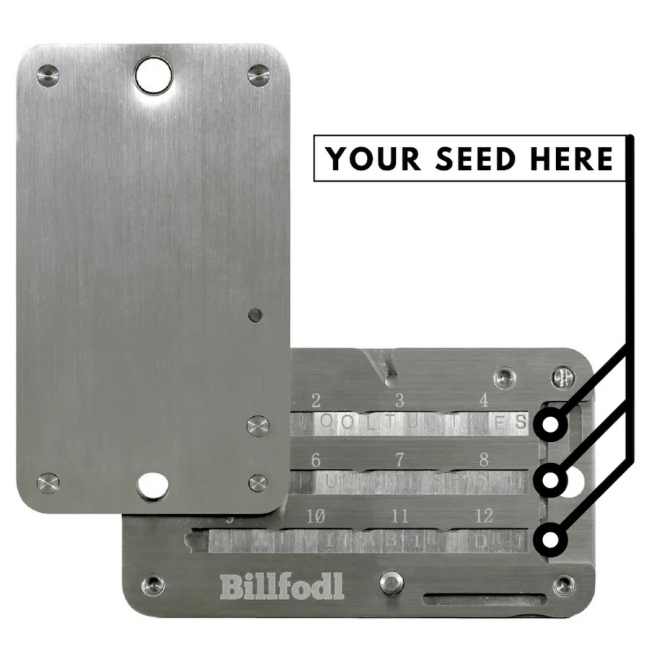
Many cryptocurrency backup devices cost over $100. The Billfodl is a slightly more affordable option that sits at $89. You can find the Billfodl on our website.
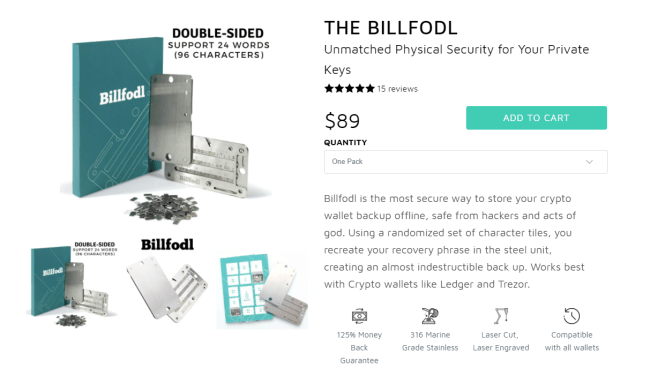
The information stored on Billfodl devices can include the following:
- Private keys
- Backup seeds—these allow users to recover private keys through use of a backup phrase
- Two-factor authentication backup codes
Info: Billfodl's are nearly indestructible by design as they are made out of marine grade 316 stainless steel. Billfodl stores cryptocurrency information offline to further protect the user's sensitive data. Billfodl is also fire proof and water proof, protecting your coins from floods and house fires; events that will ruin your hardware or software wallet.
Billfodl will survive this easily. A hardware wallet will not.
Once you’ve assembled your Billfodl, you will have a wallet-sized holding device containing private keys or recovery seeds.
The private keys and recovery seeds will help you recover currency in case something happens to your main wallet.
Remember, the backup is a list of all your private keys. Private keys reflect who owns the Bitcoins.
Software Backups (not recommended)
Before you store your private keys physically by recreating your recovery phrase in a Billfodl, backing up your Bitcoin wallet can help guard your currency information against human errors and computer failures.
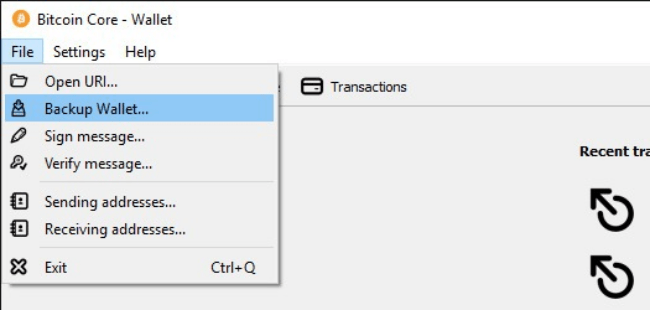
Wallet.dat
Wallet.dat is a standard method used by Bitcoin core and others to back up a wallet. The file on Wallet.dat contains keys to spend outputs, addresses, transaction info, and other types of metadata.
You can find the Wallet.dat file in Bitcoin’s data directory.
Warning: Keep in mind that the file has different locations based on the operating system.
To back up, copy the file onto an external media device such as a USB drive. Go under tools and hit “export private keys.”
To restore your backup, copy your backed up wallet.dat over an existing one in the bitcoin data section.
How to get to the wallet.dat file using the Bitcoin Core wallet
BIP 32
BIP 32 is an additional method you can use to back up your Bitcoin wallet as it verifies critical pairs from a single seed. The seed creates a master private key that can be applied to any BIP 32 wallet.
To back up the wallet, users will first create a QR code or copy the master key to a text file to encrypt and store it on an external media device.
The Best Wallet Backup Method (Recommended)
As you can see, there are many things you can do to backup your Bitcoin wallet, but there is one method that is the best.
This method is known as “seed splitting”, or what we call “sharding” here at Billfodl.
Essentially, you are taking the seed held in your Billfodl and you are separating it into 3 overlapping parts so that you need two of the three parts to recover your funds.
Why do we do this?
The main reason we split our seed is because if the entire seed is in one place and someone finds it, they can take all the coins held at that address. This is, after all, exactly what we are trying to avoid in the first place.
Info: A single Billfodl is great at protecting us from natural threats like fires and floods, but not human beings who have found the Billfodl.
If we split our seed, then even if someone finds one of the pieces, they still will not be able to take your coins because they are missing some of the seed. You can use 3 Billfodls.

Here is how it works:
- You remove the 3 shards from the Multishard box.
- Each shard is labeled with the words of the seed you need to load into it.
- Shard One holds seed words 1-16.
- Shard Two holds seed words 9-24.
- Shard Three holds seed words 1-8 and 17-24.
- Input the seed words into their respective shard units (pictures above)
- Hide each of these shards in different locations. We recommend one in a safety deposit box, one at home and one somewhere only you would think to look.
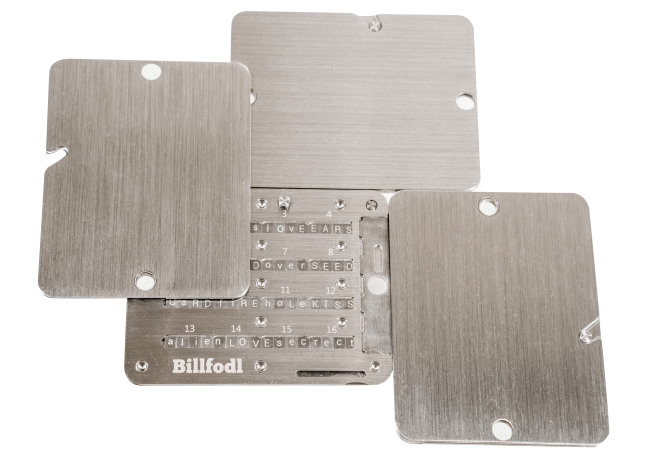
As you can see, there is an 8 word overlap between any two of the units. That means that you have some redundancy in your backups while also decreasing the risk that someone can take you coins - a win/win.
However this also means that whenever you need to recover, you will need to retrieve two of the units, but at least you can afford to lose one.
Info: The tradeoffs are therefore very obvious: splitting your seed is the way to go.
You can also backup your wallet.dat file as usual if you choose so, but again, we do not recommend it.
And if you are interested in performing this seed splitting 2-of-3 style backup method, you can pick up a trio of Billfodl’s at a discounted price.
FAQ
Is a hardware wallet necessary?
Hardware wallet is a MUST for cryptocurrency investors. This is the only way to keep private keys oofline, and this is how the investors are protected from hacking.
What is a Billfodl?
Billfodl is is the safest way to store your private key or seed words.
Why Use a Billfodl?
Billfodl gives you the peace of mind to know your cryptocurrencies are backed up on something that isn’t going short circuit, get hacked, burn up, or rust out.
Does the Trezor One Work with Billfodl?
Yes, you can use the Billfodl to back up any Trezor device, including the Trezor One.
Does the Trezor Model T Work with Billfodl?
Yes, you can use the Billfodl to back up any Trezor device, including the Trezor Model T.
Does the Keepkey work with Billfodl?
Yes, you can use the Billfodl to back up a Keepkey device.







