Disclaimer: this article includes links to products for sale on our store.
- TL;DR:
- Background
- Contacting the Owner
- The Chain Analysis
- Code Review
- Contacting the Exchanges
- Conclusion
- FAQ
In this post we are going to cover:

Plus more... Read on to learn everything you need to know about the BitcoinPaperWallet[.]com scam.
TL;DR:
The website bitcoinpaperwallet[.]com is running a wallet sweeping scam wherein users who generate paper wallets on site are not the only ones with private keys to the coins. DO NOT USE bitcoinpaperwallet[.]com to store any coins of any kind.
![bitcoinpaperwallet[.]com homepage](/images/bpws/home.png)
Background
You can skip the background of this story if you want to go straight to the research
How We Do SEO
As part of our regular work here at privacypros, one thing at top of mind for us is google rankings.
That is, we want our pages to rank as highly as possible to increase clicks and, hopefully, increase sales.
Part of great rankings is earning or building high quality backlinks to our pages.
One strategy we use to increase the backlinks going to our website is to buy existing websites and redirect them to our own pages.
Two examples of this practice were our acquisition of bitbonkers.com and bitcoinfees.info.
These sites both had earned thousands of extremely high quality backlinks and received thousands of visitors a month in organic and direct traffic.
We don’t make much (if anything) off of these pages, but they do tend to boost rankings of our other pages, and that’s why we want them.
Too Good to Be True?
We find the websites we want to buy through a multitude of methods. Sometimes we use tools like ahrefs.com. Sometimes we stumble upon the sites ourselves. Sometimes friends know the owners.
In the case of bitcoinpaperwallet.com, we were looking specifically for a paper wallet generating tool as a companion for our page on paper wallets.
This site had amazing metrics.
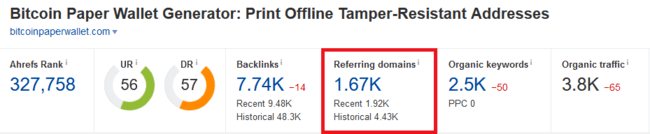
For instance, its backlink profile was insane. Lots of high quality relevant backlinks we want going to our site, such as coindesk, cointelegraph, bitcoin.com, and other major news network links like nypost and digital trends.
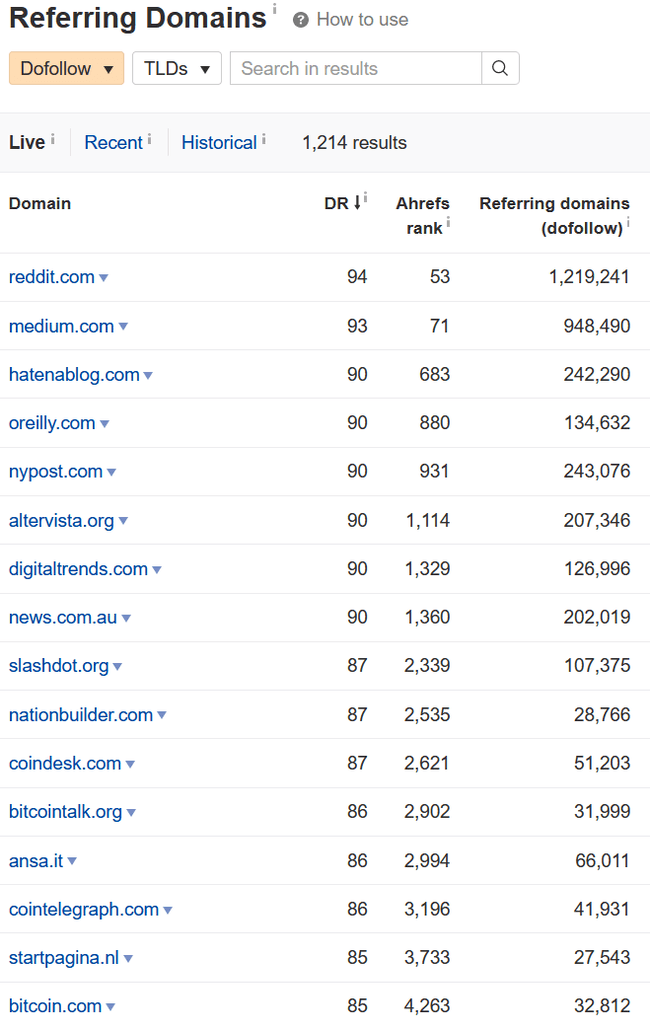
But most important of all (and most dangerously we would come to find out), it ranks #1 for our target keyword of “Bitcoin Paper Wallet”.
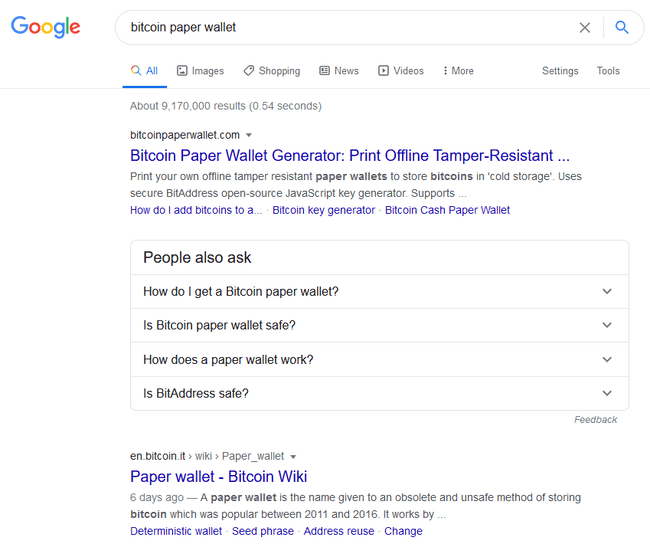
And, as it turns out, we had purchased a bootable linux installer from the site in 2017, so we assumed that surely they were a legit operation.
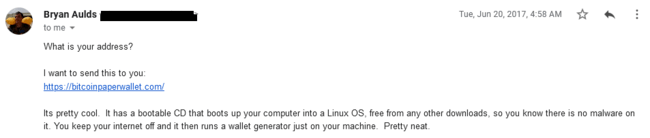
This was enough for us to try and reach out to the owner of the site and make an offer.
Contacting the Owner
After doing some sleuthing, the site appeared to belong to someone named Canton Becker who still maintains the github repository that the website ostensibly still references.
However, a note on the READ ME claimed that Canton had sold the website in 2018 and to direct any inquiries to the new owner’s email address.
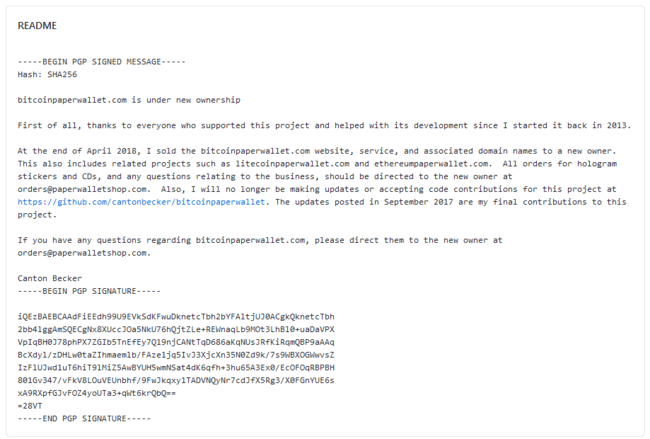
We tried to reach out to the new owner at orders@paperwalletshop.com, but with no answer.
So we reached out to Canton directly, hoping he might have an alternate way to contact him or her.
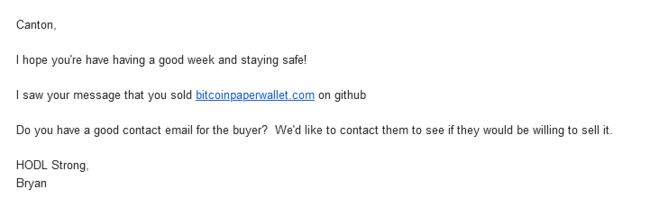
And after a little back and forth, he told us that he had received several emails over the years from individuals who claimed to have lost funds using the site.
Further research brought forth this tweet, in response to a BlockDX tweet asking for any other known hacks to add to their list.
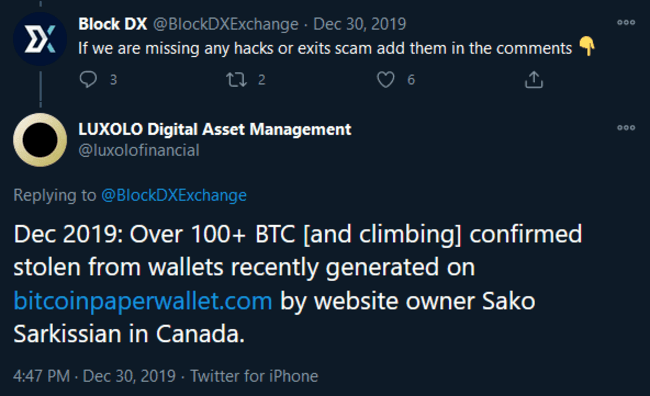
These were bold claims. Especially given how fraught paper wallets can be in terms of user error.
Were incompetent users just generating their paper wallets haphazardly and blaming the site when they inevitably lost their coins? Or…was the new owner maliciously using the site to funnel bitcoin into his own pocket (and ethereum and litecoin via paper wallet sites that were also sold by Canton to the new owner)?
At this point, we were no longer interested in the site - we didn’t want the liability.
But we did want to know if we could prove the claims about bitcoinpaperwallet.com and hopefully use our site authority to warn others.
So that’s what we set out to do…
The Chain Analysis
The first thing we needed to do was get in touch with these alleged victims.
Canton gave these individuals our email address, and one named Kunal reached out to us, with a BCC of several others as well.
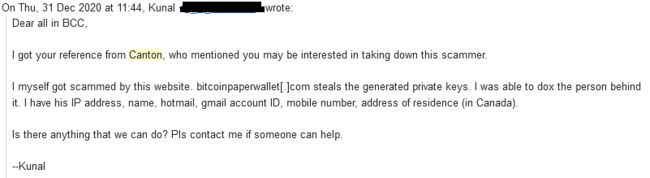
We informed kunal that we indeed intended to get to the bottom of this, but we had no desire to dox anyone until we had very solid proof that scamming had occurred.
After all, Canton had warned us that perhaps he had made some mistake coding the entropy generation process and someone unrelated to the new owner had exploited it.

For now, we needed as many drained addresses as we could get our hands on.
Kunal delivered, as he had spoken with many other victims and had collected addresses from them.
The addresses he gave us are as follows:
- 14MKVLrhaBSkqbqebQMKAqyiNhK7ir68Yh
- 1JE4yb89gEHTeZ8x9TqfN3cc6dUUSH7D5d
- 1MNdw5RKRTbatWbMTqHvntg7RLRL1WxfAC
- 17rC3BHboioNxJWvVynh7agmaiYrDTjmE6
- 19LxQ1FpJwnUokcRBNA2gnwB2FG5TbY9C5
- 18SNBJsJ1MX7qkkxfX6zKbqjLpzZK8QxjA
- 1BxPiuddFh7vz83BCFM9ZKUV75jUJyvJUv
From here, we passed them off to a friend who works in blockchain forensics, Tony Sanak.
You may know his youtube channel, Explore Crypto!
Tony then referred us to his colleague at Blockchain Intelligence Group who was able to utilize their QLUE tool to analyze the transactions. We briefed BIG’s forensic investigation team on what we were up to and asked if they could help us out.
And boy, did they!
After a few days, they got back to us.
I’ll let them speak in their own words:
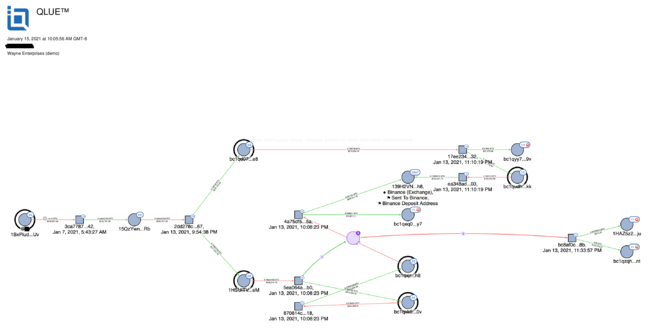
We’ve traced out some of the addresses. Here is a graph on B’s (name redacted) address. It's definitely interesting, the funds go from [that] address through several others (that each only have 1 received transaction and 1 spent) and a portion of the funds end up at Binance and the remaining funds are sitting in unspent addresses
They also provided this graphic:
Already knowing the answer, I asked them if there was any way this was incompetence.
I would be shocked if [this] was incompetence. It looks like [the funds were] purposely routed through those specific addresses, and the funds essentially get split up and go in two different directions only to end up back at the same Binance address.
In the case of B, there were two depositing transactions - both into Binance.
- Transaction hash ea348ad9acfed2881d208826a08a15335d58be223b1fa2f38c8bfbd58f357403.
- Transaction hash 4a75df5f18290563091e29856eb433c574e5005b2c4703811def6be6b24f565a
BIG continues:
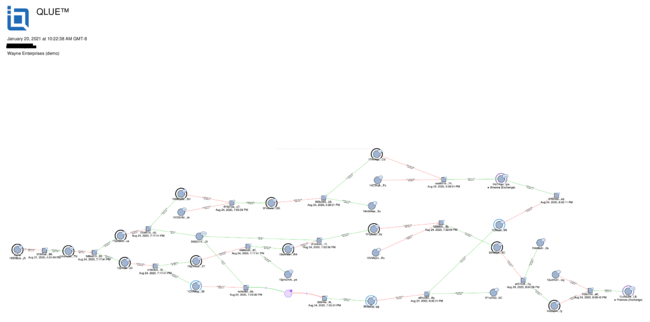
“We’ve mapped out Kunal's address and again it seems quite similar to B’s. Essentially [the thieves] funnel the funds through multiple addresses with only 2 transactions re-routing a portion of the funds back to Binance and a portion to Poloniex….The time stamps are also a good indication as most of the transactions happen within about a 2 hour time-frame, again similar to B’s case….I don't think we need to dig into the other addresses. I think it's quite clear [what is going on here].”
In the case of Kunal, there were two depositing transactions as well.
- Transaction hash 876f356c26526e26c77936f09165164e401ef8224deae4ede379e84cf56d1ead into Poloniex.
- Transaction hash aae921b285694be00fc88d140f49b7b93070d2c7e34c928a68532ea439cbb374 into Binance.
Code Review
We are still doing a code review of the live site vs the code on Github and that at Bitaddress.
Previous code reviews of bitcoinpaperwallet[.]com in the past have revealed exploits before (as shown in the video below courtesy of mycrypto.com wallet team).
In this example, the code appears to create an image of the paper wallet (which include the public and private keys) and then uploads a copy of it somewhere else - presumably to a drive folder that the owner of website controls.
This is a great thread explaining their research from 2020.
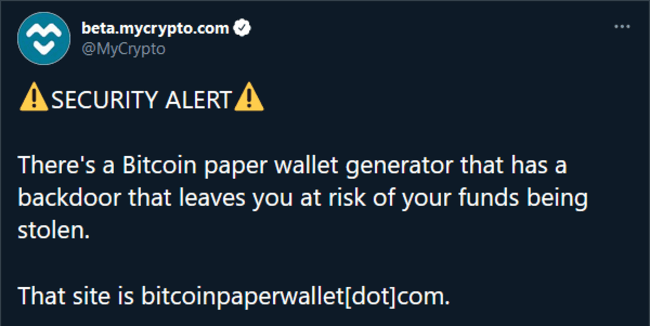
However, this method of draining wallets appears to no longer be in use, as there appears to be no more ‘imgloaded’ function any longer.
We checked this by going offline, then tried to generate an address on
http://bitcoinpaperwallet[.]com/bitcoinpaperwallet/generate-wallet.html
Then in the browser devtools network tab, we checked for any failed xhr or fetch requests, but could find none.
This would indicate that wallets are being drained using a different method now than they were in may of 2020, when mycrypto made this video.
Others online theorized that perhaps the website was generating duplicate addresses, however we generated over 10,000 ourselves and found no duplicates.
We are still researching if the duplicate generation is just a backup for the xhr request.
Code Review Update Feb 23, 2021
Following the steps from this reddit post.
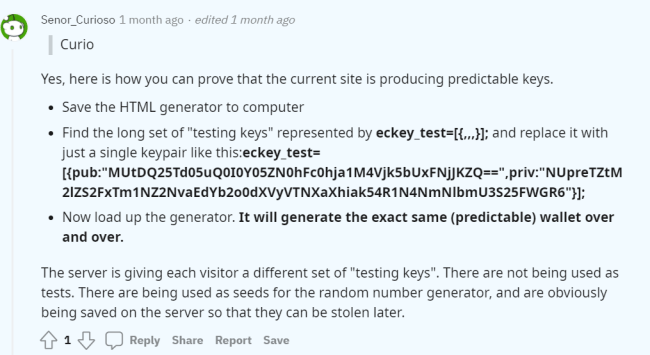
Save the HTML generator to computer
On bitcoinpaperwallet[.]com Generate Wallet, right click on the page and select “View page source”.
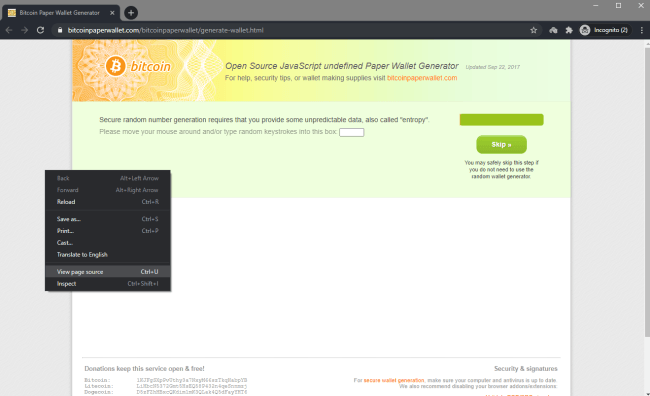
This will open the HTML page source code in a new tab.
From here, we can either select everything and paste it in a new HTML file, or right click on the page and Save as, which will prompt us to save the page content as an .html file.
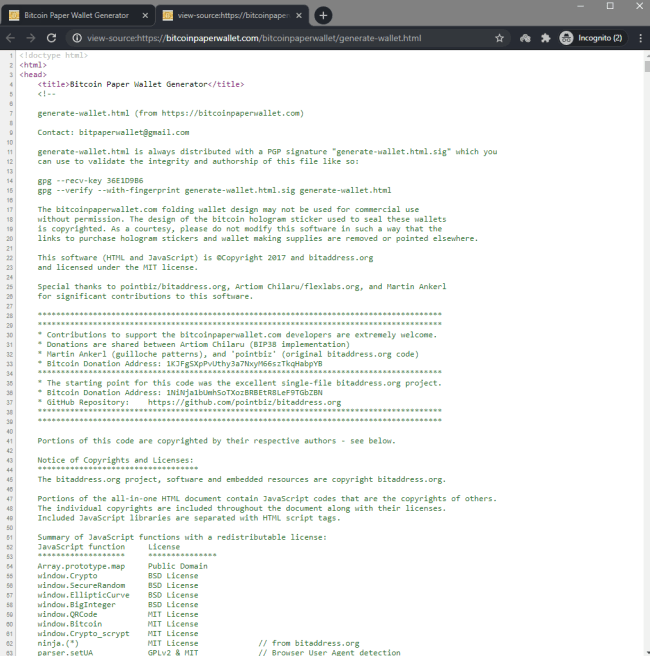
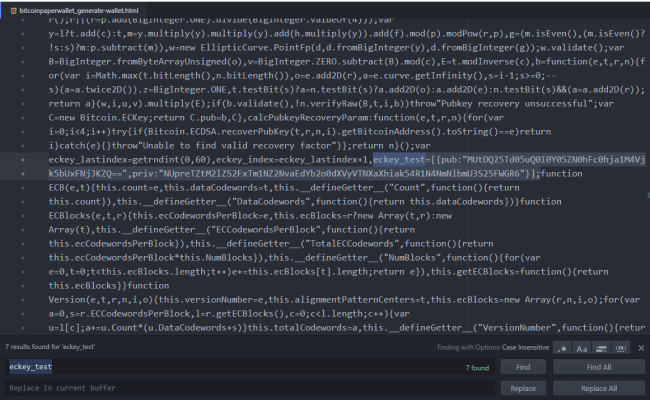
Find the long set of “testing keys” represented by “eckey_test=[{…}];” and replace it with just a single keypair
After opening the file with a code or text editor, we’ll need to search for the “eckey_test” array.
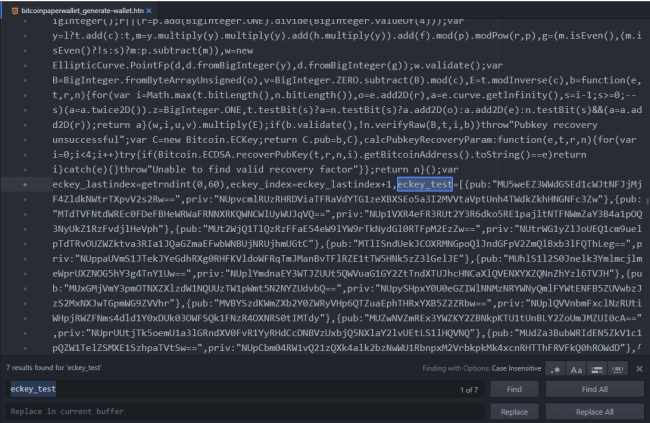
Next, we replaced the entire eckey_test=[{…}] array with just a single keypair, like the one provided in the reddit post example:
eckey_test=[{pub:"MUtDQ25Td05uQ0I0Y05ZN0hFc0hja1M4Vjk5bUxFNjJKZQ==",priv:"NUpreTZtM2lZS2FxTm1NZ2NvaEdYb2o0dXVyVTNXaXhiak54R1N4NmNlbmU3S25FWGR6"}];
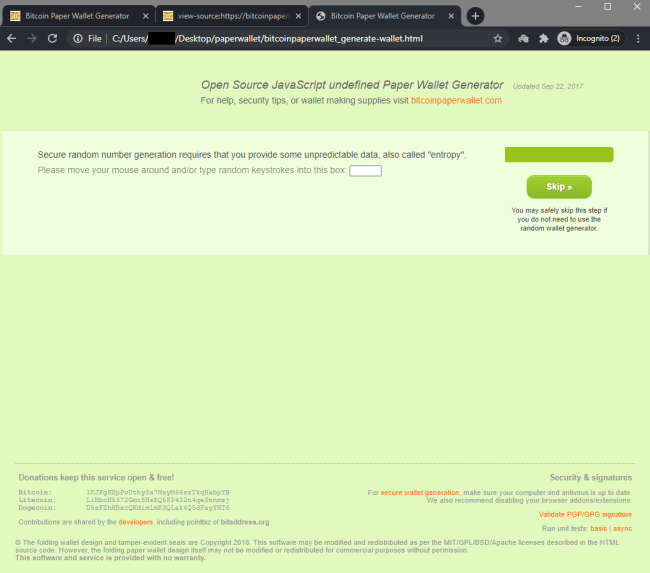
Load up the generator. It will generate the exact same (predictable) wallet over and over
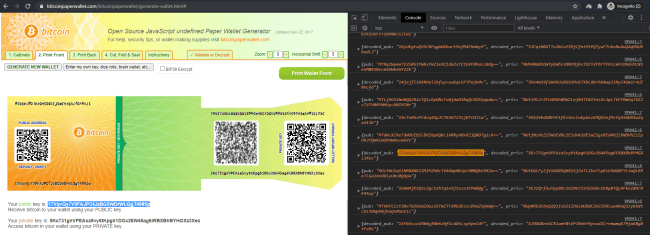
We opened the file locally in a browser:
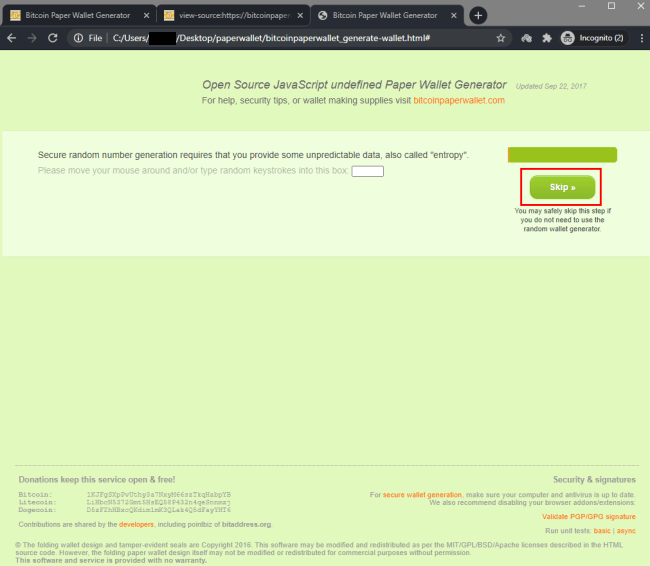
Each time a new wallet was generated, it returned the exact same predictable result.
Generating a new wallet by hitting the “Skip” button:
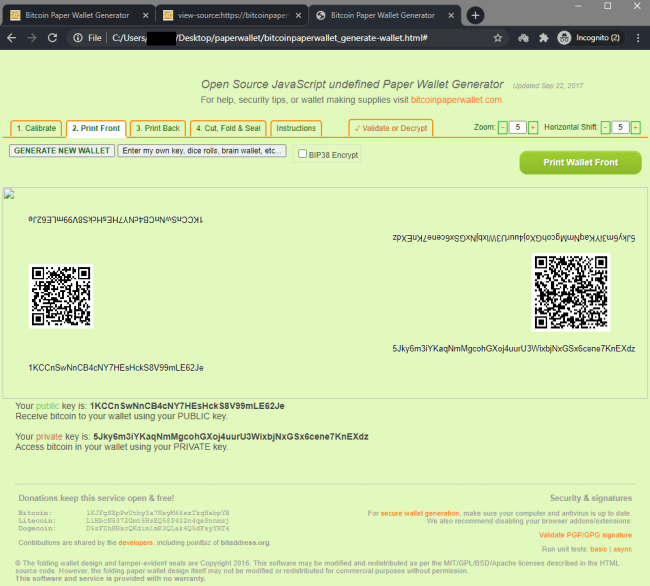
Result:
Generating a new wallet by moving the mouse and typing random keystrokes into the box:
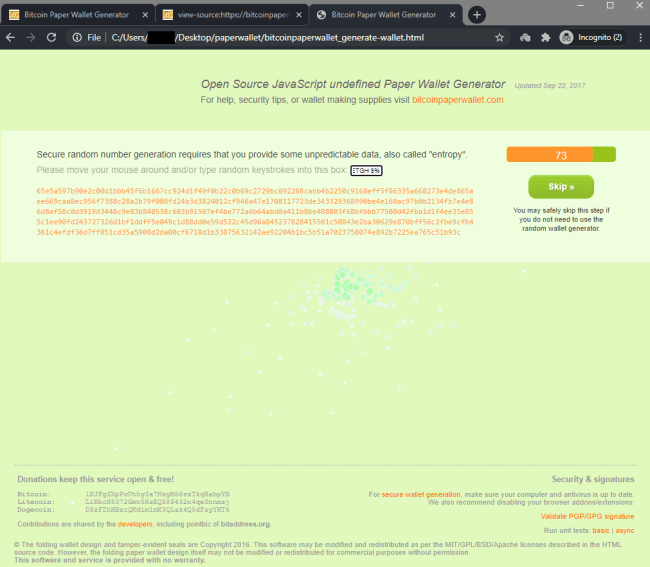
Result:
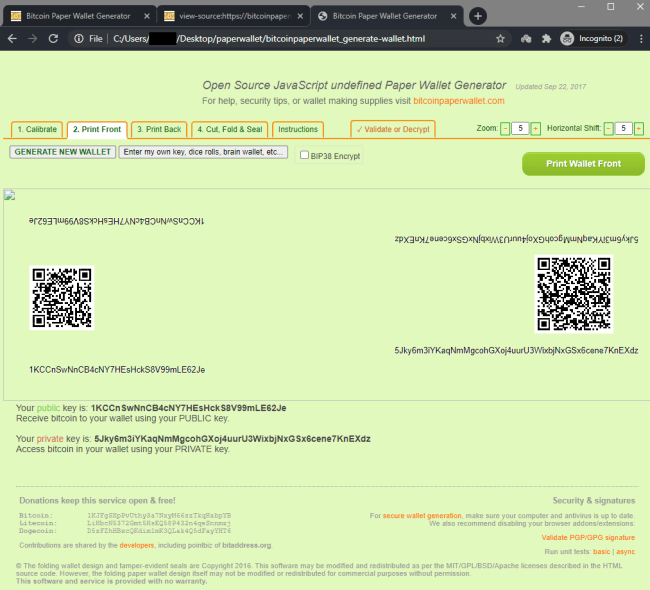
Generating a new wallet by hitting the “GENERATE NEW WALLET” button:
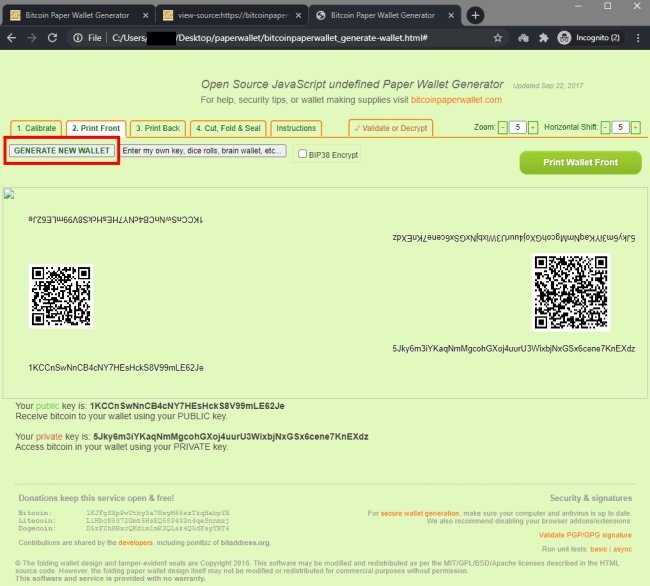
Result:
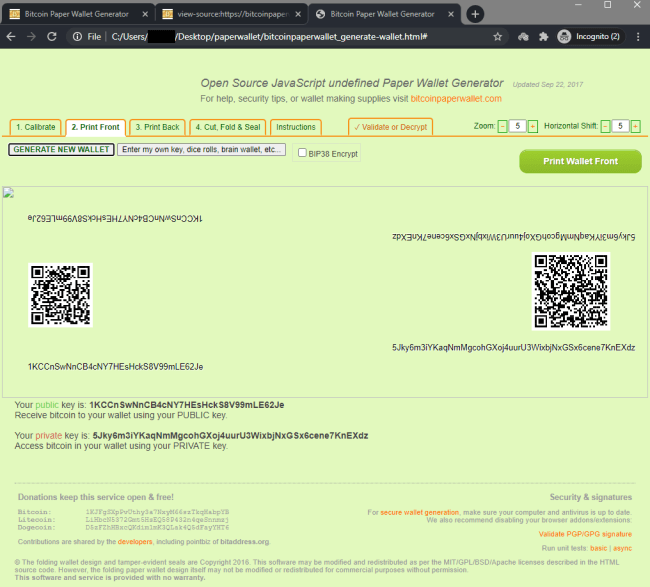
The exact same wallet was generated over and over.
Code comparison of the live site vs the code on Github
We got the generate-wallet HTML source from the GitHub repo, and after looking in the source code for the “eckey_test” array, there was return no result. The array isn’t present in the source code.
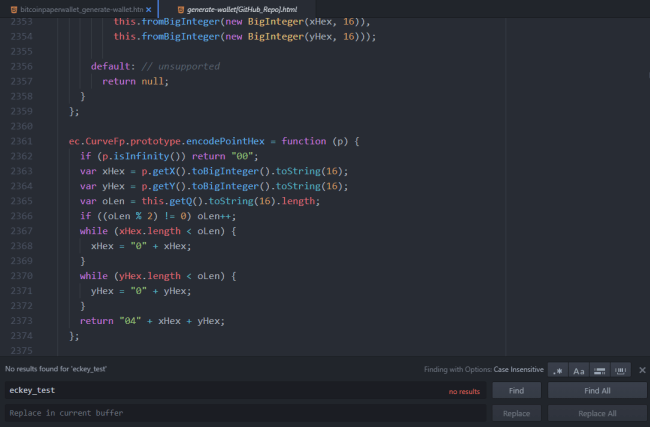
We wanted to further compare the code, so we unminified the javascript found on bitcoinpaperwallet[.]com Generate Wallet page.
For this, we copied everything between the script tags that contained “eckey_test”, and pasted it into a javascript unminifier to ge a more user friendly result.
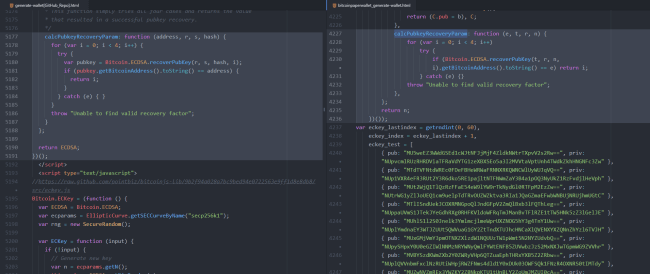
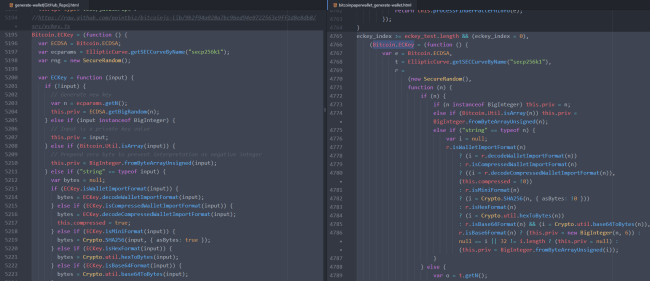
The order of the code is a bit different, but there is no “eckey_test” or “eckey_test” logic in the GitHub source.
Other info
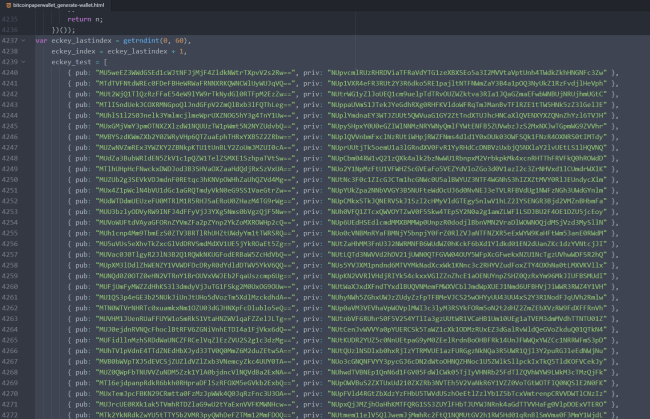
When going to the live bitcoinpaperwallet[.]com website, each time the page is loaded, another set of 60 key-value pairs is added in the “eckey_test” array.
We can see that by opening the browsers DevTools, and entering the array name:
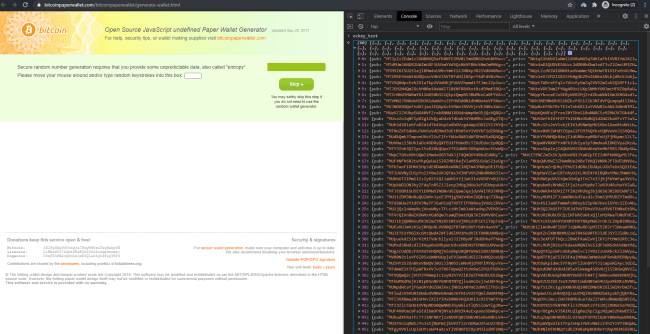
Using a short code snipped we got the decoded so called “test” keys, and printed each key and it’s decoded counterpart to the console:
eckey_test.forEach(entry => {
const decoded_testKeys = {
"decoded_pub": window.atob(entry.pub),
"decoded_priv": window.atob(entry.priv)
};
console.log(entry);
console.log(decoded_testKeys);
});
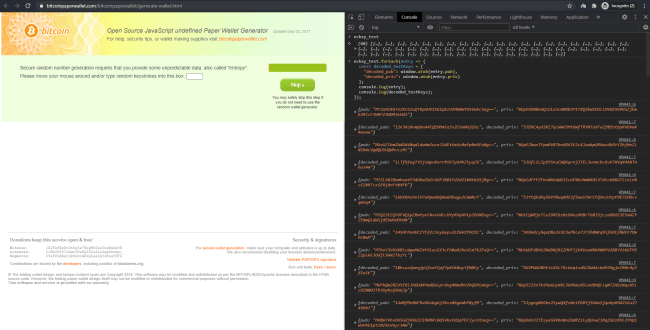
Each new wallet generated (random keystrokes, mouse movement, button press etc), just returns the decoded key-value pair from the list.
The wallet generation logic just increases the index of the “eckey_test” array by 1 each time a new wallet is generated, until it goes through all items in the array. Only after 60 wallets we’re generated, we got one that was not in the array.
Contacting the Exchanges
Of course, we wanted to let the receiving exchanges know about the stolen coins on the platform so they could help in identifying the thief and hopefully assist law enforcement in bringing them to justice.
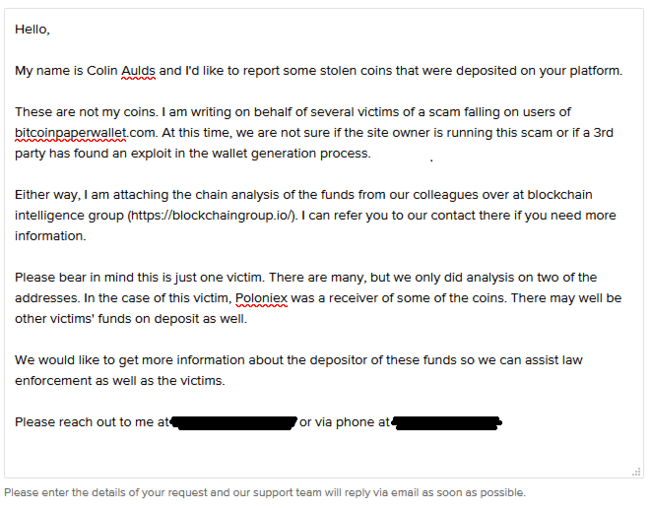
I sent more or less the same email to Binance.
Polo got back to me the same day saying they would look into the depositing transaction and see what they could come up with.
Binance was basically the same.
Understandably, in both cases, we were told that since these accounts do not belong to us, they would not share updates with us regarding the progress on the case. They did tell us that they would cooperate with any law enforcement agencies regarding the matter and that the victims should file a police report.
Our victims have since filed police reports in their various jurisdictions, but it is unlikely that the police will act on this information.
Conclusion
This investigation is ongoing and will be updated as we continue our research. We do not yet know for certain whether or not the site owner is himself reponsible for these wallet sweeps or if some third party has found an exploit in the site source code.
Given how many times the site owner has been informed of the issue and his refusal to fix it certainly indicates he may be responsible for the stolen funds.
In short, under no circumstance should anyone be using wallets generated on bitcoinpaperwallet[.]com to store any amount of their Bitcoin. Whether by negligence or maliciousness, the site is not reliable and the evidence on this page should be enough to prove it.
FAQ
Is Bitcoinpaperwallet.com a scam?
Yes, if you use bitcoinpaperwallet.com to generate a paper wallet, you will have your coins stolen. DO NOT use bitcoinpaperwallet.com to generate a paper wallet.