Disclaimer: this article includes links to products for sale on our store.
- Chapter 1:
- History of the Faraday Cage
- Chapter 2:
- How a Faraday bag works?
- What Does A Faraday Bag Do?
- Are Faraday Bags Effective?
- Chapter 3:
- Why Are Car Thefts Increasing?
- What Is A Signal Killer Faraday Bag?
- Preventing Keyless Car Theft With a Faraday Bag
- Chapter 4:
- What can a Faraday bag protects you from?
- What Should I Store In A Faraday Bag?
- What Should I Store In A Faraday Cage?
- Objections to owning a Faraday bag
- When Should You Use A Faraday Bag
- Faraday Bags vs Mylar Bags
- Chapter 5:
- 1050D Ballistic Nylon
- Verification Window
- 5th Gen Device Shielding
- Triple Layered, Dual Paired Seam
- Easy Access
- Summary
- Dimensions
- Free Shipping
- Easy Returns
- Secured Payments
- Customer Support
- Chapter 6:
In this post we are going to cover:

Plus more... Read on to learn everything you need to know about Faraday bags.
Chapter 1:
You’re here for one of two reasons. Either you’re wondering what a Faraday bag is, or you want to know why you should buy one. And you’re going to get the best answers to both.
Adding one to your lineup of cybersecurity tools can be very powerful, but only if you know how to use it.
From a technical perspective, they are copper foil-powered enclosures that block all radio signals.
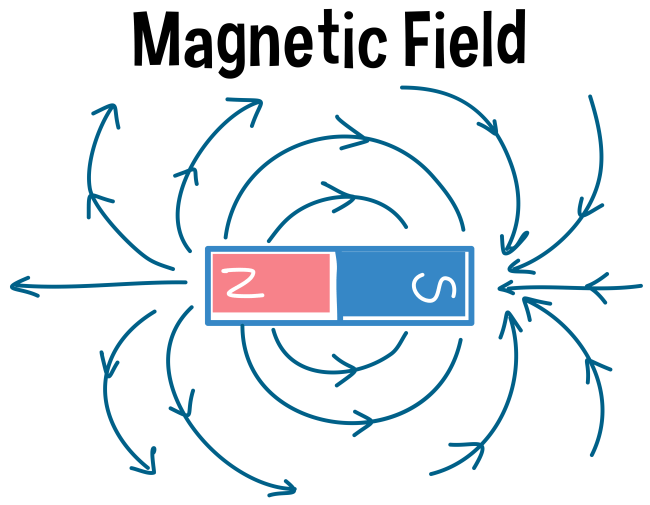
From a practical point of view, Faraday bags play the role of a safer “airplane mode” for your phone or a vault for your contactless credit card.

What is most fascinating about Faraday bags is that they are able to bring military-grade isolation in a small and portable form factor.
They tell a modern-day story of David defeating Goliath, as millions of dollars worth of surveillance gear can be defeated whenever you put your electronic devices inside these thick layers of copper and plastic.

History of the Faraday Cage
The Faraday Cage was first conceptualized by Michael Faraday in 1836 and previously observed in the documented experiments by Benjamin Franklyn and Jean-Antoine Nollet a century before.
Info: Faraday cages and Faraday bags are some of the most effective and affordable ways to create protection from radio frequencies.
Since their discovery, Faraday cages have been used in various places ranging from chemistry labs where precise and sensitive measurements are required, to US Military and NATO computer centres where any unwanted radio emission must be blocked for security and equipment precision considerations.
The popularity of these EM (electro-magnetic) and RF (radio frequency) shields is so great that they spawned the “tin foil” internet meme.

You can even see them play an important role in the plot development of “Breaking Bad” prequel Better Call Saul.
Saul Goodman’s older brother Chuck McFill suffers from a rare condition which makes him vulnerable to radio waves, so he covers his house in tin foil and avoids using any electronic devices.
Saul is shocked to see his brother, Chuck, plaster the house in tinfoil to repel electro-magnetic waves.
Info: Faraday cages are impractical for personal use and may be a little too elaborate for particular everyday needs. Somebody who simply wants to secure a mobile phone, internet connection, or computer by blocking radio frequencies can simply make use of a Faraday bag.
For this small-scale purpose you don’t have to shield the entire room, building, or environment to isolate individual devices – it’s enough to just purchase an affordable Faraday bag or build your own by alternating layers of plastic and aluminium.
Chapter 2:
Faraday bags are small, portable, affordable accessories that block electromagnetic fields. They are more practical versions of the mighty Faraday cage.

A Faraday bag is a type of Faraday cage.
It protects electronics from being damaged by radio frequency interference (RFI) or from an electromagnetic pulse (EMP) by not allowing radio frequency or electromagnetic pulse waves to pass through the material.
It goes by a lot of names such as RFID bag, RFID blocking bag, or EMP bag.
How a Faraday bag works?
It creates a completely enclosed space that is surrounded by a mesh of conducting materials.
When an electrical field on the outside of the Faraday cage interacts with the material, it causes the charges within the protected space to be distributed in a way that cancels the effects.
It also works to protect against radio frequency interference.
This way the hackers, thieves, or government agencies who are trying to track your phone or any other device will not be able to get to it because of the outer layer of the Faraday bag.
Info: Unlike other solutions we've given in this guide, this is the only one where you don't have to trust anyone or anything except the laws of physics which is why a Faraday bag is the most reliable way to prevent your phone and location data from being monitored and mined by third parties.
An added bonus: Faraday bags can keep other data and property safe too!
What Does A Faraday Bag Do?
In a nutshell, they block all radio signals ranging from Wi-Fi and Bluetooth to RFID (used by credit cards and car keys) and GPS.
Whenever you want to prevent unwanted attacks on your electronic devices, it’s a good idea to place them in a Faraday cage.

But when you find yourself in a situation where you need to use your devices on the go while employing the maximum amount of security, Faraday bags will get the job done.
Warning: When it comes to securing your electronic devices, switching to “airplane mode” or manually turning off every communication feature (Wi-Fi, Bluetooth, GPS, infrared, RFID) does not suffice.
Competent hackers will be able to make it seem like everything is disabled, while they exploit any kind of data. As prominent NSA whistleblower Edward Snowden explained during his interview with Joe Rogan, electronic devices aren’t really turned off until you remove their battery.
Edward Snowden was an NSA whistleblower who fled to Russia in 2011 after leaking thousands of classified documents to a handful of journalists.

In an era when the largest majority of phones, tablets, GPS gadgets, smart watches, and remote controls come with unremovable batteries, being able to have a physical “off” switch is a blessing.
And having a Faraday bag to completely block all signals is precisely this shutdown button.
The best kind of security is the one which enables prevention of attacks by decreasing the attack surface.
Info: And as long as your devices are inside a Faraday bag, no signal will be capable of penetrating its thick layers of intertwined copper mesh and plastic.
You prevent malevolent attacks before they can even happen.
This way, you can stop worrying about stealthy remote hacks forever and allow your phone, car keys, Bitcoin hardware wallets, and RFID credit cards to rest in a safe environment while you don’t use them.
Are Faraday Bags Effective?
Info: Faraday cages are so efficient and affordable that they are used and trusted by US and NATO military operatives under the Tempest standards.
Chemists who need to do precise measurements in their laboratory experiments also employ Faraday cages, so that no external radiation can influence the results.
Conversely, Faraday bags are the small and portable versions of Faraday cages.
Unlike elaborate setups that isolate an entire room or building, Faraday bags fit into your pocket and provide the same kind of security for the electronic devices that fit inside.
The build quality standard is maintained, so that the thickness of the intertwined copper and plastic layers insures the same signal-blocking effects.

In a nutshell, Faraday bags grant you the benefit of having the protection that NATO operatives have, but in a light and portable form factor.
The fact that you can take this security with you anywhere without raising suspicions is yet another advantage.
People around you will think that you’re carrying a cheap nylon wallet or some sort of common bag.
Easily blending in improves your privacy, and not exposing your devices to hackers in the first place is an excellent security practice.

Therefore, Faraday bags are effective as both radio signal repelling units that remove Bluetooth, RFID, GPS, and Wi-Fi exploits, but also as basic items that secure your electronic devices without ever raising anyone’s suspicion.
On the Let’s Talk Bitcoin podcast, Andreas Antonopoulos stated that he kept his hardware wallets in a faraday bag. In addition, @patrickwagner, a digital security expert, calls a Faraday bag “a must have.” The threat of a solar storm or EMP blast to our society presents itself as one of the greatest dangers to security in any modern country. If we are going to digitize our monetary system at any point in the foreseeable future, it’s time to take proper security measures to protect our assets today.
Chapter 3:
Car theft is something that has been observed since the invention of the automobile. In the times when cars had door locks and ignitions with a mechanical key, people found ways to pick the lock and hot-wire the car{ rel=”noopener” }.
With the advancement in technology, electronic locks were introduced, and now cars have a central computer that is locked with an electronic key.

This is one of the best ways to prevent thieves from stealing your car. However, as with every technology, thieves have found a way around this security measure and have started using devices called code grabbers to perform what is called a SERA (or ‘Signal Extender Relay Attack’).
Info: The thief utilizes a device that looks for the signal emitting from your key fob and amplifies it, allowing the thief to unlock your car and start the ignition.
SERA attacks have become more common everyday and the cases of theft have been increasing considerably. People are often perplexed by the question of how to prevent keyless car theft?
Why Are Car Thefts Increasing?
Police departments around the world are seeing a huge increase in car theft in recent years.

These thefts have left police departments baffled because most of these cars were locked with an electronic locking system which is one of the safest auto security systems available.
After investigating, you will find many videos showing thieves using a device to open the lock of the car and stealing it without tampering with the vehicle directly. So, what is this device that is being used to steal these cars?
Info: This device that the thieves have been using is called a key fob code grabber.
Thieves have become tech-savvy and have started using this device to catch the radio frequency of the key fob, cloning it, and then using the newly made duplicate signal to open the door of the cars and drive off.
Modern car key fobs work with the help of electro-magnetic signals. When the car key is near the car, there is a radio frequency between the car and the key fob.

When the user presses the unlock button on the remote of the car, the doors opens since the car sees the signal. The only way in which this theft can be stopped is by using an RFID blocking bag, also called a Faraday bag.
What Is A Signal Killer Faraday Bag?
The Signal Killer Faraday Bag is designed on the basis of the Faraday Cage.

The cage is made of conductors that do not let any other electric signal or wave enter. This principle is also used in building airplanes; the planes are designed in such a way that if struck by lightning the electrical force cannot enter the inside of the airplane.
Info: The Signal Killer Faraday bag functions in much the same way. It blocks out all the waves that are entering or exiting and spreads them around but does not let them pass.
So anything that is kept inside the bag cannot be accessed by outside electric or magnetic waves and vice versa.
Faraday bags have been used by the military and police for ages to protect technological evidence such as phones, laptops, smartwatches, or other hardware that has important digital data inside.
This technology is now being used by the public since data and car thefts are increasing considerably.
Preventing Keyless Car Theft With a Faraday Bag
Now the question is, how can you prevent your car from being stolen by using Faraday bag?
Warning: As we explained above, the thieves are using code grabbers to extract signals from the car key fobs and duplicate or extend them so that the car system gets tricked and the car door unlocks easily.
With a Billfodl Faraday Bag, the signals from the car keys will get blocked, so the radio frequency of your car keys will never reach the thief’s device. This will save your car from being stolen.
Advice: Because most of these thefts are happening at home, it is best to keep the Signal Killer bag where ever you normally keep your keys.
Just get into the habit of dropping your keys into the bag as you come in the door. Then you no longer have to worry about your car getting stolen in the middle of the night.

A Faraday bag can be a great way to add additional protection to your electronic devices.
Few items are as effective for so little money as a Faraday bag, and we should all be using one.
If you have any questions, our team of experts here at Billfodl are here to answer them!
Chapter 4:
The threats that a Faraday bag protects against could be naturally occurring or manmade.
What can a Faraday bag protects you from?
An example of a naturally occurring threat is a solar storm. Believe it or not, solar storms which come from the sun have the potential to wipe out power grids and electronics here on earth. One such storm is known as the Carrington Event, and occurred in 1859. At that time, humanity didn’t have nearly the level of reliance on electronics that we do today. Yet at that time, telegraph systems in Europe and North America stopped working, the equipment sparked and gave shocks to the operators and even started fires.
If a solar storm of this magnitude were to occur today, it would widely damage and disrupt electronics such as cars, computers, and power grids. Even smaller items might be affected such as a common USB drive. Such a solar storm occurred in 2012 of a similar magnitude but it didn’t hit earth (it missed by just 9 days).
In 1989, another solar storm hit the Earth and Canadians took the brunt of it, although it wasn’t of the same magnitude as the Carrington Event. Still, power grids went offline and some 6 million Canadians were left without electricity - some for hours and some for days.
Info: As it happens, there is no reliable way to predict solar storms or when they may happen.
Man-made threats are predicted to come in the form of nuclear or EMP bombs. Nuclear explosions send out electromagnetic shockwaves that could wipe out electronics and power grids just like solar storms. A man-made bomb that emits electromagnetic shockwaves could even be detonated some distance above a target in order to be effective. This topic was even brought up among GOP presidential candidates during the 2016 election race.

The fact is that, despite the possible threat to electronics, people and nations are not prepared to defend the technology that we are becoming increasingly reliant upon.
What Should I Store In A Faraday Bag?
There is no finite answer to this question.
Ultimately, it comes down to any item that can be remotely hacked and that you would prefer it not to be.

The following list gives common items one might store in Faraday bag.
- mobile phones
- laptops
- Bitcoin hardware wallets
- car key remotes
- credit cards
- passports
- smart watches
- tablets
- building access cards
Warning:Mobile phones and tablets are easy to attack via Bluetooth or WiFi. Credit cards can be used to spend money via contactless payments by placing a scanner close to your wallet. Furthermore, the radio which unlocks your car can be remotely intercepted and replicated to cause you damages. The bitcoins you keep in a hardware wallet aren’t absolutely safe from remote attacks either.
The Cheshire Police in the UK are recommending drivers to keep their car keys in a Faraday bag to prevent thieves from being able to clone them. All they would need to do is get close to your keys, without even seeing them, unless they were protected in an RFI-blocking Faraday bag.

USBs and Bitcoin hardware wallets will fit inside Billfodl’s smaller Faraday bag. If you want to keep a phone or small tablet, you’ll want to get the bigger one.
During his December 2018 presentation from the 35C3 conference, Josh Datko of the wallet.fail team has demonstrated how he was able to send attacks to Trezor and Ledger hardware wallets.
In the event of supply chain attacks where an extra RFID antenna is placed in your hardware wallet, it becomes very simple to remotely control your device and send coins to arbitrary addresses.
Accordingly, it’s definitely better to keep your hardware wallet in a Faraday cage if you want to be 100% sure that nobody can attempt to remotely hack your device.

If you’re targeted by governments or elaborate hackers, it’s very likely that they will attempt to compromise all of your devices.
Even if you’re a law-abiding citizen, our modern-day surveillance capitalism may find excuses to make this type of backdoor access completely legitimate and possibly mandatory.
Info:In such a scenario, it becomes civil duty to make use of Faraday cages and bags whenever you get the chance, so the attack surface gets limited and you can offer proper protection to your private property.
Here is yet another argument in favor of Faraday bags: since they are small, portable, and easy to disguise in everyday items such as wallets (or even conceal in your suitcase or backpack), they grant you a degree of plausible deniability.
Nobody will feel suspicious when they see one, and it’s easier to disguise them as common objects.
And for only $15 for a small Faraday bag or $25 for a large one, the price you pay to protect your precious data and belongings from RFID, Bluetooth, and WiFi attacks is extremely small in comparison to more elaborate security setups.

The cost of purchasing rolls of plastic and tin in order to build your own Faraday bag is even smaller, but getting the right kind of result takes some time and experimentation.
And…it won’t be nearly as doable.

What Should I Store In A Faraday Cage?
Faraday cages are for large objects that you don’t carry around.
Protecting your internet router from hackers outside your house, or making sure that nobody tries to remotely attack your desktop computer are only two of the most popular use cases.
Just keep in mind that military organizations which comply with the Tempest standards make use of Faraday cages to prevent electrical signals and noises from being intercepted.
Advice: While you might argue that your data and internet devices aren’t subject to the same precautions as military secrets, it’s also worth considering that your private property is no joking matter and you’re responsible to protect it.
Often times Faraday boxes are confused with Faraday cages, but the differences can be narrowed down to scale.
The former are smaller and used for safe long-term storage of electronic devices, while the latter refer to larger surfaces that get temporarily or permanently isolated from outside radio frequencies.
For more details regarding Faraday cages and their practical use cases, check out the great variety of YouTube videos on the matter. Not only that they provide thorough explanations, but they sometimes also features complete DIY guides that allow you to build your own Faraday cages.
Objections to owning a Faraday bag
So what does that mean for Bitcoiners? Why is it all the more important for us to consider such threats and take appropriate measures? And is it an ‘appropriate measure’ to get a Faraday bag?
Advice: If you’re a Bitcoiner with any significant amount of Bitcoin, or if you’re a Bitcoiner who ever intends to have a significant amount of Bitcoin, then it is absolutely worth it to get a Faraday bag.
Common objections to owning a Faraday bag are that it’s unnecessary if you have your mnemonic seed (private keys) backed up on your Billfodl already, and that the likelihood of an EMP blast is low enough that you don’t want to spend the money.
The risk-reward ratio of owning a Faraday bag is heavily tilted in favor of getting one. The probability of the risk may be low (or it may not be), but the cost of a Faraday bag is also very low.

It simply doesn’t make sense for a Bitcoiner to argue that the world should be supported by a digital monetary system that allows individuals to be completely sovereign over their money, and then on the other hand to argue that individuals who do so should be careless enough not to protect valued electronic devices which greatly enhance the security of accessing said money.
So you have a Billfodl already. That definitely is a higher priority than owning a Faraday bag, EMP bag, RFI blocking bag. And if our electronics do go down due to some form of disaster, Bitcoiners will not have access to their funds unless they also have access to functioning electronics that can be used to interact with the bitcoin network.

And in such a case, if a Bitcoiner should have to use an untrusted computer to access funds, simply using the private keys could be a very risky endeavor and should be avoided. If only that Bitcoiner had stored a tablet or Bitcoin hardware wallet in a Faraday bag, all would be well.
When Should You Use A Faraday Bag
Ultimately, the answer comes down to the scale of your signal-blocking operations and your expectations for portability.
If you want to protect your mobile phone or Bluetooth-capable devices from external attacks and you’re traveling or on the run, it’s simply better to get a Faraday bag.

On the other hand, if you want to isolate an entire room or building from radio frequencies, Bluetooth intrusions, and unwanted WiFi signals, it’s a lot better to make use of Faraday cages.

Interestingly, thick metal trash cans in which you insert a plastic bags can be excellent Faraday cages for your mobile phone, tablet, hardware wallet or laptop.
However, they are not very portable and walking around with them will definitely raise suspicions.
Therefore, if you simply need to isolate small devices, then it’s definitely better for operation security (op-sec) to carry a Faraday bag in your pocket, suitcase or backpack.

At the end of the day, the distinction is very simple: Faraday cages are for open spaces where you use devices that require no mobility.
These devices might include:
- internet routers
- desktop computers
- chunky laptops that you never carry with you
- your HAM radio set if prepping for SHTF
While Faraday bags are for securing your mobile phone, car key fobs, and items like bitcoin hardware wallets on the go.
Certainly, you can also use a Faraday bag in your house if you want to avoid redecorating the walls or raising suspicions about your mental sanity whenever someone visits you.
Faraday Bags vs Mylar Bags
Mylar bags are very popular solutions to store food on the long term.

The fact that they have Aluminium foil on the inside means that your vegetables will stay fresh in the fridge for an extended period of time.
Info: However, they are not considered to be efficient against RFID (radio frequency identification), Bluetooth, or WiFi signals.
In comparison, Mylar bags are thinner than Faraday bags – the former have a thin and minimal Aluminium foil, while the latter is built from a thick layer which alternates plastic and Aluminium.
Certainly, you can stack multiple Mylar bags in order to achieve results that are similar with those you get with Faraday bags.
A popular Reddit post has examined the issue only to discover that two Mylar bags are not enough to block AM radio signal.
Advice: In conclusion, if you are truly concerned about the security of your electronic devices and want to block remote attacks, it’s definitely better to not compromise on layers of plastic and aluminium by opting for a Faraday bag.
The difference between a Faraday cage and Faraday bag is mostly in the size and portability of the item.
Faraday bags are great for small items that fit in your pocket, while Faraday cages are more used to protect stationary objects or entire rooms of gear.
There are several options for Faraday bags on the market, but we think ours is pretty damn good and it comes in at a great price as well.
Chapter 5:
A Faraday bag is a very simple product, but many people are still confused about how they work and what they do.
1050D Ballistic Nylon
Our Faraday bags are made out of water-resistant 1050D Ballistic nylon, known for its intense strength and hardiness, because your electronics should be safe from more than just radio frequencies.
Verification Window

Seeing is believing, which is why our large Faraday bag sports a device preview window to confirm signal cutoff and battery life on all electronic devices inside. Don’t trust. Verify.
5th Gen Device Shielding

Blocks WiFi (2.4 & 5GHz), Bluetooth, cell signals (5G & 4G LTE+), GPS, RFID, and radio signals with 60-80dB average attenuation offer 5th Gen device shielding assurances.
Triple Layered, Dual Paired Seam
Three layers of high-shielding fabric on all sides are sown together with dual paired seam construction, making the bag durable and ready to work in inclement conditions.
Easy Access

The double roll and velcro closure means accessing your electronics is a breeze. Our bags are designed to keep radio frequencies out, not you.
Summary
- Military-grade faraday bag designed for law enforcement forensic investigators, also used for executive travel, personal security, EMP and CME protection
- Shields cell phones, GPS units, electronic toll collection transponders (like E-ZPass), key fobs, or other similar size devices from ALL wireless signals
- 5th Gen device shielding assurance
- EMI shielding & RFI shielding
- Three layers of high-shielding fabric on all sides with dual paired seam construction
- Blocks WiFi (2.4 & 5GHz), Bluetooth, cell signals (4G LTE+), GPS, RFID, and radio signals with 60-80dB average attenuation
- Closable pocket on back to place company/agency information
- Water-resistant ballistic nylon outer materials
- Double roll and Velcro closure
Dimensions
Large Bag
Outer dimensions: 9.75” x 9.5” x .1”
Inner usage dimensions: 9.5” x 5.5”
Small Bag
5” x 3.25” x 0.25
Free Shipping

All US orders and International orders of $120
Easy Returns

No questions asked - just 125% money back guarantee
Secured Payments

All card payments are secured through Shopify payments
Customer Support

Get free and fast email/chat support with our in-house crypto experts
Chapter 6:
Do Faraday bags really work?
Yes, they do. They work like a shield against outside influences. They are easily transportable, packable, lightweight and are not very expensive.
Do Faraday bags block GPS?
When you place a GPS device inside a Faraday bag, it cannot receive or transmit potentially disruptive radio frequency signals.
Why do Faraday bags stop working?
A high quality Faraday bag should never stop working. However, cheaper bags can wear out if opened and closed often, This is where finding a high quality bag is important.
Is it harder to steal keyless cars?
Security experts say that it takes about three minutes to steal a car without keyless entry and that it’s almost impossible to steal a car when the key fob is inactive or in sleep mode.
Can my phone be tracked if Location Services are off?
Location History is a feature that keeps track of the locations you have been and any addresses you type in. If you turn it off, your device will use only GPS to know where you are. That being said, there is no way to be sure location services and GPS are truly no longer active unless you use a faraday bag.
How do I know if someone is tracking my phone?
The truth is, its very hard to know if a sophisticated attacker is tracking your cell phone. And…you are almost certainly being tracked by many of the apps you have installed. When in doubt, its better to assume your phone is being tracked.
Why would I need a Faraday bag?
If you want to protect any kind of electronic device from being tampered with remotely, then you must use a Faraday bag. A Faraday bag works as a protective shield against any incoming and outgoing radio signals.
Do Faraday bags block WIFI?
Yes, they do. The Wi-Fi signals cannot penetrate the copper mesh inside of a Faraday bag.
What is a Faraday bag used for?
Faraday bags are used for securing your mobile phone, laptops, car key fobs, and items like bitcoin hardware wallets on the go, credit cards, passports, smart watches, tablets, and building access cards. They prevent remote tampering of these devices from those who would steal data off of them or try to wipe or track them from a distance.




