Disclaimer: this article includes links to products for sale on our store.
- Chapter 1:
- Chapter 2:
- Why do you need to secure your data?
- Who do you need to secure yourself from?
- Determine your Paranoia and Threat Model
- Chapter 3:
- Use a VPN
- Use Tor
- Public WiFi
- Chapter 4:
- Browser Fingerprinting
- Choice of Browsers
- Adblockers
- Search Engines
- Chapter 5:
- Messaging
- Social Networks
- Chapter 6:
- Educate Those Around You
- Flashed Routers
- IoT Safety
- Chapter 7:
- Use a Password Manager
- Use Two Factor Authentication
- SMS Two Factor
- 2FA Apps
- Hardware Keys
- Chapter 8:
- Does Your OS Protect You?
- Why you still need to get antivirus software
- Update Apps and Software Regularly
- Chapter 9:
- Encrypt Your Devices
- Backup
- Chapter 10:
- Use Cryptocurrency
- Use Coin Cards and BitRefill
- Use Disposable Credit Cards
- Chapter 11:
In this post we are going to cover:

Plus more... Read on to learn everything you need to know about securing your personal data.
Chapter 1:
Since the dawn of the internet, our lives have become even more digital.
Everything has shifted; from financial services to entertainment to medical records.
While digitalization has made our lives easier in so many ways, it has also brought new challenges. For example, the average American had their passwords stolen four times in 2019.

The latest data by the Pew Research Center shows how Americans see their digital lives. The current state of mind when it comes to personal data and online security reveals two things:
- 72% of Americans think that all their online and cellphone activities are tracked. The trackers, they believe, belong to advertisers, tech companies, or other firms.
- Three-quarters of Americans worry about how firms and the government use their online data.
In this Pew research, very few knew how their information was collected. Even less knew what exactly someone is doing with their info. That was a state of things in 2019. In 2020, COVID-19 pushed personal and business life online. The lines between offline and digital life are blurrier than ever.
Distancing yourself from digital monopolies like Google and Amazon is now more important then ever. Unfortunately, protecting your online privacy is something that you need to start doing today, and we’ll cover everything in this article.
Chapter 2:
Why do you need to secure your data?
Many people stick to the mindset “It’s OK for a company to track me because I have nothing to hide.” A similar mindset, “I don’t need to worry about online privacy, no one cares about me anyway” doesn’t work in 2020. It’s time to learn who is tracking you and why.
Collecting personal information is a multi-billion dollar industry. Someone obviously does care about which sites you visit and where are you located. The real money is in selling personal data in bulk to third-party companies. And this is all legal.
For example, it often doesn’t occur to people that Google or Facebook services are not free. The currency in which you’re paying for these services is your personal data. Google and Facebook shares your data with advertisers, third-party companies, and intelligence agencies.
There are also illegal groups that produce malicious software to collect your data. These crime groups will pay for banking information and personal identities, and they buy this info in bulk. Either way you look at it, your digital life is not safe. You have to take active measures to secure and protect it.
Who do you need to secure yourself from?
In short, there are three main “institutions” that you need to protect yourself from.
Hackers will aim to take your data and information and sell it for a profit. In recent years, ransomware has also appeared whereby they will take your device hostage unless you pay them a fee.

Advertisers will look to mine your data. As mentioned above, companies such as Google and Facebook are in the market to get your data. This ranges from social networks to even scanning your private emails.
Governments often spy on their residence, and no-one showcased this better than Edward Snowden. Unfortunately, most governments around the world spy on their residence and it can be useful to protect yourself against this even if you aren’t doing anything illegal.

Determine your Paranoia and Threat Model
Being paranoid used to have a negative connotation, but not anymore. Unfortunately it’s true that many companies and institutions are looking to get their hands on your data and information. In this article we recommend a lot of practical advice that you can use to protect yourself online.

However, implementing everything on this list is a challenging and time intensive task. While we would love for you to implement everything, we know that’s not realistic, but we hope you will try at least a few. To determine what steps you should take, determine your threat model.
Advice: Your threat model is what you're afraid of. If you're avoid of hackers, then clearly an Antivirus is going to be the key, if you're worried about the government then locking down your social networks and internet should be on top of your list.
To determine which steps would be useful to you, have a look at our menu items, and if you’re interested in a topic then reading the introduction should help you understand it better.
We’ve closed each section with a piece of advice. These advice sections will help you take the first step with relation to that topic. We’ve also put helpful links throughout so you can find out more about a specific topic.
Chapter 3:
When you’re online, it’s relatively easy to track you using your IP address, and your activities. The main culprit in this is your ISP. They keep information on your online activities; when you use it, how you use it, and so on.

Unfortunately, they use this information themselves, hand it over to advertisers and even give it to the government if required.
Advice: So if there's one thing you do on this list, then protecting your internet should be that one.
Use a VPN
As mentioned above, securing your internet connection is important, and getting a VPN is an essential step.
In short, a VPN routes your device’s internet connection through your chosen VPN’s private server. This means that your ISP can only see encrypted data between you and the VPN, and the rest of the world will see your location as that of the VPN server.
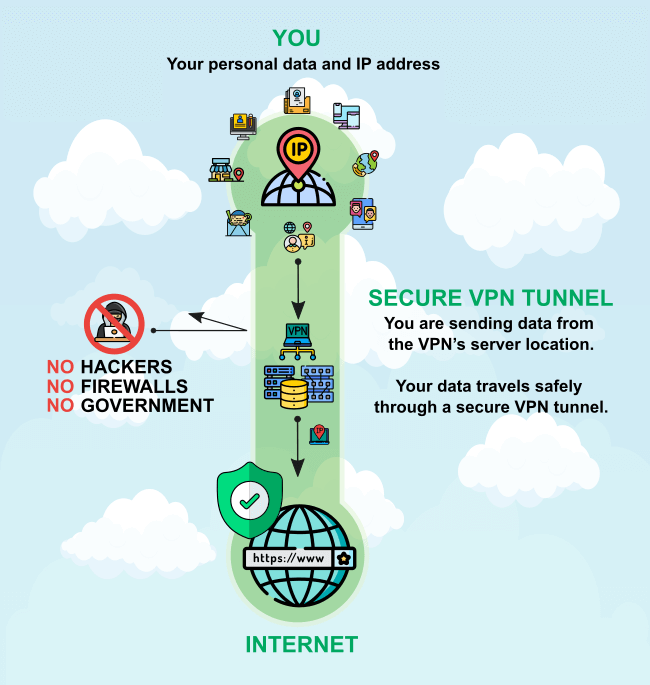
You can see the benefits of using a VPN immediately. Your location is hidden from trackers. This is especially useful when you are on a public Wi-Fi. VPN also enables you to access region-locked content. Also, when torrenting, your ISP won’t be able to log your activity.
Info: Your data travels safely through a secure VPN tunnel. If anyone was sniffing your connection, it would look like you are sending data from VPN's server location. This is particularly useful for businesses, now that many employees are working from home.
Additionally, there are many services around the world that are region restricted. For example Netflix different content depending which country you’re in, and BBC iPlayer is only available in the UK. With a VPN you’re able to spoof your location to get access to a greater range of online content.
Advice: A VPN will protect your ISP from tracking you, and will help hide your real location. The best VPN service right now is NordVPN, and you can find out more about the best VPN services here.
Use Tor
Unfortunately, VPNs aren’t perfect, and there are cases when they are blocked. TOR is a great alternative.
If you have no other means of protecting your digital life, Tor will give you anonymity. Tor otherwise known as The Onion Network is a free, open-source network, and browser that provides online anonymity.
You should use Tor primarily to browse the web privately. Keep in mind that Tor can’t anonymize network activity from other apps, e.g. Steam, Messenger, or Skype. To access the Onion Network, you first need to download the Tor browser. It is available for Windows, Mac, Linux, and Android.
Tor works through a network of worldwide servers or nodes. The traffic from your browser is first encrypted as the data travels to and from each node. Then, as it reaches the destination, its decrypted layer after a layer. If someone intercepted your browser traffic, they could only get the data from the last node. The information about the source - you - and the information about the destination are encrypted.

The main reason why Tor isn’t a perfect privacy solution, even for web browsing, is its speed. Tor is very slow compared to regular browsing due to all encryption and decryption happening in the background. You can use it to access the region-restricted content, but it is noticeably slower. Not to mention that you are in no way protected from security risks. Compared to using a Tor browser, even the cheapest VPN option offers better privacy and speed, for an average user.
Warning: Depending on your country and your ISP, using Tor can be prohibited or labeled as suspicious. If you use Tor to log in to your personal accounts such as Gmail or Facebook you are leaving snippets of personal data, so it's best to avoid doing that. Tor is even less suitable for torrenting since torrent protocol shares the IP addresses between the peers.
All in all, if you need a very high level of anonymity while browsing the web, the Tor browser in combination with the VPN would be an ideal solution. Tor alone can help you when you have no other options available, but it’s far from a perfect solution for everyday use.
Advice: Download the TOR Browser today and see what it's like surfing the internet with it. You will also be able to access the "dark web", just watch out as it has a lot of illegal content on it.
Public WiFi
We’ve all connected to at least one public WiFi in our lives, and many of us use them regularly, especially where data charges are high. Unfortunately, public WiFi comes with it’s own dangers.

The biggest danger is that anyone on the network can “sniff” your traffic. Though they might not be able to get everything, they will often be able to get a lot of useful information. Information such as access to your social networks, what websites your visiting, and more. If the person is then dedicated enough they can use the information they’ve collected for malicious purposes.

Additionally, all of your connection is unencrypted and the person providing the public WiFi can see everything that you’re doing. Now it’s unlikely that someone like Starbucks would spy on their free WiFi but what about that corner bistro or that bargain clothes shop you go to? Collecting and selling private data could be an additional revenue source for them. Even worse than that, they can use the WiFi to infect your device with a malicious software.
Advice: Have a look at all the WiFi networks you've connected to previously on your mobile phone and think about all the activities you did while on them, and how someone could have accessed them. If the thought scares you, then consider getting one of the VPNs listed above.
Chapter 4:
Above we discussed protecting your internet connection on the whole. However, it’s not enough to hide your internet connection if your choice of software gives you away, or if your browser flat out collects data on you.
Browser Fingerprinting
Similarly to human fingerprints, each computer system has a unique fingerprint which allows it to be identified and segregated for marketing purposes. In fact, if you have an extremely unique system, it could even be used to persecute you, should you do anything illegal.

Interestingly, even websites can use this information to target you with more relevant ads, or find exploits in your system. For example we can determine which languages you speak, what permissions we have on your system, where you’re based, what device you’re using, and a lot more.
Advice: You can use a service like AmIUnique to see how unique your system is, and if you stand out from the crowd. The answer will probably be yes.
Choice of Browsers
One of the biggest factors that come into play when talking about your web browsing is your choice of browser. Chrome is the most popular browsers but it’s also the worst choice. Firstly, it’s owned by Google, a company known to willingly share your data. It definitely uses your data for advertising purposes, and no-one really knows how much information it really collects.

Luckily, Chromium, the software that Chrome is based upon, is open-source and audited. Therefore, the probability of it having any backdoors or tracking capabilities is limited. For this reason many companies have used it to develop their own browsers.
Advice: While there are a whole range of secure browsers, we'd recommend using Brave. It's based upon Chromium so you're able to use all of your browser extensions as before. However, it removes unnecessary features and ads anti-tracking measures by default.
Adblockers
Apart from changing your browser, you can also use adblockers to change what your browser tracks and what information the websites you visit can collect about you. There’s a whole range of adblockers that you can use, and these vary browser by browser. However, to get started we’d recommend Ghostery, Privacy Badger and AdBlock.
These adblockers will help keep your data on a lockdown. Unfortunately, the downside is that with each additional extension your fingerprint becomes more unique. One way to overcome this is that many VPNs are now providing a built in AdBlocker that will filter out Ads (and in some cases trackers) before they even reach your browser.
Advice: Download PrivacyBadger, and have a look at how many tracking requests it's blocking on some of your favourite websites.
Search Engines
Google keeps coming up in this article. So if you haven’t got the picture yet, they collect your data to sell to third parties. So it’s not surprising that their main offering, Google Search, is the biggest culprit.
The biggest way a company can collect data on you use by offering a free search engine, and this is what Google, Yahoo, and Bing all have in common. Despite their difference in size, their end goal is the same, and it’s not to provide you with relevant results. It’s to be able to get know your personality.

By using your search history, Google can create a profile of you and by combining data sets they can use this data to profile your family, your neighborhood, your county, and so on. Using a secure search engine can help put a stop on companies tracking you.
Advice: Try out DuckDuckGo, which is the most private search engine around. Their latest offering also helps block ads, removes trackers and ensures HTTPS everywhere.
Chapter 5:
Though many people don’t realize it, even your private communications aren’t so private. It’s one thing that companies use our online behavior to target ads for us, it’s another that they scan our private messages!
Emails are the most commonly scanned pieces of private communication. While no one actually reads your emails individually, and there are systems in place to ensure this doesn’t happen, it’s still not a pleasant thought to know that someone has access to our discussions.

As always the biggest culprit here is Google with Gmail. Many people have a GMail account yet what most people don’t realize is that Google scans your keywords and uses this for advertising. Don’t believe us? Just write “find attached” in your email and if you don’t attach a file Google will let you know because they scan your emails!
Personally I’m not worried about Google using my search history because it does mean that I find what I’m looking for quicker and easier. However, my emails are my own and I only want myself and recipient(s) to know it’s contents.
Info: Additionally the pure HTML of an email can contain information about you that can lead to malicious parties tracking you down.
For this reason, alongside a VPN the second most important tool you could get if you’re worried about being tracked is getting a private and secure email account.
Advice: Test the free version of Protonmail, to find out that using a private email is just as easy. Private and secure emails are easy to use and work with traditional mail services too.
Messaging
On the note of private communications, we also use a range of apps to message each other daily. In fact, most of us communicate with our friends on more than one platform. For example you may be messaging on iMessage, Instagram, TikTok, WhatsApp, Slack, and Facebook Messenger in a single day.
The reality is that most people use a wide range communications method purely based on the people they are surrounded by. While some of these are OK, others I wouldn’t trust as far as I can throw. On the better side we have the likes of WhatsApp (though it is owned by Facebook) and Viber, while we’re pretty certain that Facebook Messenger and Google Hangouts monitors your messages.
Unfortunately, most of these communications aren’t encrypted or secured in any way. That means, that just like emails, it’s likely that they are monitored. So similarly to emails, we would recommend avoiding most major communication methods if you don’t like being tracked.
Advice: Try Telegram or Signal to discover that private messaging apps are just as good, if not better, than traditional messaging services.
Social Networks
OK, so in this section we could write thousands of words. However, it’s unlikely that you’ll be reading that because you have better things to do with your time. So in short we’ll some up the two core issues with social networks, which one worries you more is up to you. Unfortunately, these apply to any major social network that you may use; Twitter, Facebook, Instagram, Pinterest, TikTok, etc.
All major social networks are free. If we know something, if a product is free, then you’re the product. This is more true here than anywhere else on the internet. Social networks profit of your engagement and they collect thousands of data points on each and every one of it’s users. Not only do they use these data points for advertising, they also use it to get you to engage more and spend even more on the platform. It’s a never ending circle, and unfortunately, most people keep using them as there are no alternatives and all of their friends and family are using them.
The other concern is that social networks are designed to be, well social. Therefore, by default you’re account, what you publish, and so on is public. Unfortunately, most people aren’t aware of this and never change their settings. While you might not think that a cute picture of your dog Buster is anything to worry about, this is exactly where you’re wrong. Remember those security questions that we all hate, well that’s exactly where that information is useful. Social engineering is one the rise and it’s exactly for this reason, so if possible, make nothing public.
Advice: This will take some time, but read these articles on how to lockdown your privacy on Facebook, Twitter, and Instagram. You can find similar information for your chosen social network by googling it, followed by the words "Privacy settings".
Chapter 6:
First and foremost it’s important to protect yourself. However, you should never forget about those surrounding you.
If you’re part of a household, whether your the head of the house or not, you need to educate them too. Unfortunately, the number of people who are still unaware of the dangers of the internet is huge. Whether it’s your sister-in-law being too public on TikTok, your younger brother torrenting, or your partner using the same password everywhere, you should take a social responsibility to help educate them.

Similarly, if you work in a company, you should look to educate your peers and if need be the management too. We’ve worked in too many companies where we’ve witnessed unfathomable mistakes and privacy holes.
Educate Those Around You
The best way to help protect those around you is probably the simplest - simple education. You can either share this article with them, or take your time to talk to them and explain the dangers. We’d recommend that instead of using extreme examples, you use credible daily facts and figures. For example many people were outraged when they learned about the Facebook Cambridge Analytica scandal but not many people ended up taking action to help secure their social networks afterwards.

However, if you discuss with them how your data can be used against you and how on a daily basis social engineering is used to steal valuable information, they are more likely to listen. That is from our experience anyway.
Of course, you will know the people around you the best so choosing the method of education is completely up to you.
Advice: Create a Privacy Handbook together with your family or coworkers. Not only is it educational, it's also a great bonding exercise.
Flashed Routers
Another great way of protecting those around you is by using a flashed router. In essence a flashed router allows you take a better control of your WiFi network, and most importantly run a VPN client on it reliably.
Almost all electronics you own comes with pre-installed firmware. Firmware is the essential software that enables the device’s primary functionalities. Your Wi-Fi router is no different. Flashed routers are generally easier to use, and you can purchase them preflashed, as the process of flashing isn’t easy and requires you to know your default router login details amongst many other information.
FlashRouters.com offers a selection of flashed WiFi routers. The main attraction of routers flashed with DD-WRT comes from built-in VPN capabilities. You can use FlashRouters Privacy App to sign in to your favorite VPN provider, at a router level, in a single step. Supported VPN providers include ExpressVPN, NordVPN, and Surfshark, among many others.
Advice: Purchase a flashed router from FlashRouters and start protecting your immediate family and friends. We recommend one with an ExpressVPN app for the best speed and reliability.
IoT Safety
One of the biggest worries these days is IoT safety. Many of us now have Amazon Alexa or Google Home in our apartments. In addition to that more and more Internet of Things devices are coming to the market regularly.

Whether it’s a fridge, a coffee maker, or even just CCTV cameras, the world of IoT might make our lives more comfortable but it opens us up to a whole new level of risk. Unfortunately, many of these devices are planned and created with practicality in mind, and security and privacy takes a back seat - if that.
Over the years there have been countless IoT scares. The most famous case of IoT hacking is CloudPets where by not only did the company leak user details, the hackers were also able to hack into their teddies and spy on it’s owners. If you’re a parent there’s not much creepier than something like that.
Advice: Try to research the privacy of any IoT devices you use. Additionally, a flashed router running a VPN should help provide you with some safety.
Chapter 7:
As Security Magazine reports, Americans had their password stolen at least four times in 2019.
The websites breached are not some small, unnoticeable outlets, either. Facebook alone had three major data breaches exposing over 808,500,000 accounts. First American Corporation tops them with 885,000,000 accounts breached. Microsoft, Zynga, Canva, and Adobe are also a part of this list.
Companies and websites should transform your password from text to unreadable content. This process is called hashing. There are simple and complex hashing algorithms. But, there is no way of knowing which one is somebody using, unless they state it. When a data breach occurs and passwords are hashed using a simple algorithm, or worse, not hashed at all, it’s easy for hackers to crack your password.
As an answer, some sites ask you to use a password that is a mix of lowercase/uppercase letters, numbers, or symbols. When these passwords are hashed even using a simple algorithm, they are more difficult to crack. Now thousands of websites need registration, and it is hard to remember each password. The next step hackers rely on lies in the way we behave online.
People tend to use the same or similar password for many websites. We often use passwords that are easy to remember.
Info: Gaining access to one of your password makes it easier for hackers to guess your other passwords.
Use a Password Manager
These days any respectable browser provides an integrated password manager. However, the best way to handle your passwords is by using a password manager. A Password manager does exactly what it says on the tin - it manages your passwords. All password managers integrate with your devices so that they are easy to use. Most will even help with passwords for Apps on your mobile devices.

To access your password vault you only require a Master Key and Master Password to be able to decrypt it’s contents. The way they are set up is so that even the companies providing the service won’t be able to access your passwords without these. Therefore, make sure you keep these somewhere safe and secure, as if you lose them you’ll have a lot of password resetting to do.
Advice: The best password manager at the time of publication is Dashlane. However, as with all services we recommend doing your own research before deciding which password manager to go with. While they are very similar at the core, they do offer different features and pricing.
Use Two Factor Authentication
One thing you are going to want to set up on any online account that allows it is Two-factor authentication.
You may already be familiar with one form of 2-factor authentication(2FA) in the form of authenticator apps like LastPass authenticator or SMS two factor.
SMS Two Factor
2FA requires the use of a cellphone. To login to your account or to change your password, a service provider sends you the code via the SMS. It’s assumed that the only person with access to your phone is you, but if you are sim-swapped, this won’t stop someone from stealing your accounts.
2FA Apps
For this reason, SMS two factor is widely considered to be insecure these days. That is why people have resorted to 2FA apps where the second password is not texted to you, but rather generated on your phone itself. This way, an attacker would need to have access to your phone or the service servers that are generating keys.
2FA is easy to set up and once set up it won’t cause any inconvenience to your life, or using the apps.
However, even these apps are not perfect. That’s why hardware keys were invented.
Advice: Enable 2FA on the apps that you use daily, and where any financial information is involved such as your bank and PayPal. This should only take a few minutes and will significantly help, it might even be more important than using different passwords.
Hardware Keys
Universal 2nd Factor authentication or U2F is the new standard for secure login. U2F requires the user to have a key token device and a browser (Chrome or Firefox) that supports the U2F. With this hardware token device, such as YubiKey, you can safely login to any account.

The U2F process is based on asymmetric cryptography. Your token device contains a private encrypted key. The compatible browsers recognize your public key. It’s worth noting that the encryption of your private-public key pair uses a complex mathematical algorithm. The pair has no meaning without each other. The hacker would have to use an incredible amount of resources to crack private key based on the public key.

This approach prevents so-called middle-man or phishing attacks. That is if someone gains access to your public key they have no use of it because it is paired only with the private key stored on your device.
Advice: Purchase a Yubico and start protecting your immediate family and friends. We recommend one with an ExpressVPN app for the best speed and reliability.
Chapter 8:
In the internet days of the past, viruses were once the biggest threat there could be to your PC. The antivirus software came as a solution. But, in 2020, the term antivirus software has a new meaning.
Nowadays, true computer viruses have become a rarity. USA Cybersecurity Magazine says computer viruses comprise only 10% of all malicious software. Worms and Trojans are more frequent, but they too are in the shadow of more dangerous types of malware.
Ransomware encrypts all or some valuable data on your hard drive. To get your files back, you need to pay the attacker for the decryption key. Spyware gathers your data, including sensitive information such as your bank account details. Adware displays unwanted ads on your machine. The list goes on. There are botnets, phishing attacks or malicious cryptocurrency mining attacks through browser hijacking.
Does Your OS Protect You?
There is one myth we need to dispel first. Mac OS X is not invulnerable to malware. The myth arose from the fact that PC always had a larger market share. Also, the UNIX-based operating systems, such as OS X were harder to attack. In reality, there is nothing stopping hackers to try to inject ransomware on Mac machines. If anything, hackers assume Mac users are wealthier since they spend more on their machines.
As our lives became digitalized, Microsoft and Apple responded with preinstalled security services. Since Windows 10, Microsoft offers a decent solution through the Windows Security Center, and Apple has Gatekeeper.
Advice: Make sure the firewall and virus scanner built into your OS are enabled. While they aren't top of the line they will provide at least a basic level of protection.
Why you still need to get antivirus software
Top antivirus solutions moved far beyond traditional antivirus protection. While some attackers want to crash your system, there’s far more money in attacks like ransomware. If you use your PC or Mac for anything more than checking email, you need the protection by modern antivirus.
You can get services such as VPN, data protection, and online vaults for your data, all in one package. First, you’ll want an antivirus that covers as many threats as possible. Antivirus companies detect threats and update their databases quicker than operating system manufacturers. This is essential for preventing zero-day attacks. Additionally, decent AVs will have additional tools such as; web security, rescue mode, safe file deletion, vulnerability assessment, and much more.
Unfortunately, an antivirus does have a small effect on PC performance due to the constant scanning. However, if you run a half way decent system you won’t notice. It’s a bit more noticeable on mobile devices but the added safety is worth the minor impact on batter life in our opinion.
Advice: Test out Bitdefender with it's 30-day free trial to see how it can help make your every day life safer and more secure. You might even discover that your computer already has a virus or malware on it, as many devices do.
Update Apps and Software Regularly
Name any operating system or major software and someone probably has tried to hack it. Unfortunately, this isn’t an exaggeration, this is the real world. If there are enough people using an app or software then there is profit to be made from hacking it. Whether it’s by collecting personal data, or even worse collecting financial data, someone will find a way to make money from it.

You’ll regularly notice your iPhone or Windows 10 PC informing you that there will be an update when you next shut down. In fact, you might notice this quiet regularly. While some of the time this is to add some extra functionality to the software, it’s often to patch security holes. Unfortunately, no matter how hard providers try, 99% of software has a vulnerability in it. This is why it’s important to regularly update your OS, software, and Apps.
Advice: While most OS and software has automatic updates enabled by default. However, check that this is the case and ensure that automatic app and software updates are also enabled.
Chapter 9:
We’ve talked about protecting your internet, password, family, and your computer. However, there’s something that’s possibly more important than any of those. That’s your data.
When worrying about your data there’s two things you have two worry about; data theft and data loss.
The most prominent example of data theft is jocularly referred to as “The Fappening”. It was a serious breach whereby in 2014 naked pictures of over 500 celebrities were leaked online. Unfortunately, this is just one of many examples of data theft happening in out world today, and it’s not limited to celebrities.
On the other hand, data loss is about you losing your data. Whether it’s the classic case of the dog eating your laptop, or just dropping your iPhone down the toilet.
Advice: Knowing that your data is backed up is extremely important.
Encrypt Your Devices
The most obvious reason why you should have your hard drive encrypted is theft. If somebody steals your laptop, for example, it is a lot easier for that person to gain access to all your info. If you are a business user, anyone who gains access to your HD can get all your business information. Even if you are a desktop user, ransomware attackers are counting on you not caring to protect your data.
This is the reason why modern operating systems come bundled with tools to encrypt your HD. Apps like BitLocker for Windows or FileVault for Mac both offer software encryption. There are also HDs and SSDs that have built-in hardware encryption capabilities. You just have to make sure to turn them on. HDs with hardware encryption is a bit pricey, but do offer better protection.
Info: Software encryption is a more accessible, cheaper, and more often used solution. Software encryption usually relies on the AES-256 encryption standard. AES-256 encryption makes the content of your HD, including the operating system if you choose so, unreadable to anyone who doesn't have the decryption key. Ideally, the only person with the decryption key should be you.
Things would all be fine if there wasn’t one issue with the encryption and decryption. They rely on complex mathematical equations to cipher the content. So, encrypting or decrypting your entire SSD can take quite a while. Microsoft, for example, estimates it takes 5 hours to encrypt 500GB. Of course, you can always choose to encrypt only portions of your HD to save time.
Advice: Encrypting your HD, especially if it contains your business data, can help when you're a victim of a ransomware attack, therefore you should encrypt your drives today. Either use the built in tools or look for alternative solutions.
Backup
So we’ve covered protecting your data from unwanted people. But what about protecting your data from human nature and misfortune?
Info: Luckily, this is just as easy as many of the other steps on this list. All you need to do is select a backup provider that you like, set it up and it will take care of the rest. If you're lucky you'll never have to actually use it.
However, if you’ve ever been in a position where you’ve lost some data, you’ll know how important this is. The perfect backup plan is called the 3-2-1 methods. Which means you should always have 3 copies of your data. 2 of them should be backups and 1 should be offsite. In layman’s terms: Your PC, a local External Hard Drive, a Backup Service.
Though there are many classic “backup” services such as GDrive, Dropbox, and iCloud that many of us use, these aren’t perfect. The reason for this is that they do not back up everything on your computer. So while they are a step in the right direction, they aren’t a complete solution.
Advice: Try Backblaze. It's a full fledged backup provider that will help securely and safely back up all of your data. It has a free trial to test it out and costs just $6/month after that.
Chapter 10:
Unfortunately, one of the most important things in life is the least under your control. That’s your financials. Unfortunately, you receive your card from the bank, but beyond that everything else is in their control. You could always stuff your cash under the mattress or buy real gold, but those are old school tactics. We’ll show you some great ways of helping you get better control of your financials with ease.

Use Cryptocurrency
The best way to keep your purchases and assets anonymous is by using Bitcoin. Bitcoin has big potential for anonymity at its core, but it takes some effort to use this potential.
Any Bitcoin user’s identity is hidden behind a Bitcoin wallet address. Bitcoin transactions happen on the Blockchain network. The Blockchain is a public and distributed ledger of transactions. This means everyone can see every transaction ever made between two wallet addresses.
The key to keeping anonymity when using Bitcoin is safeguarding your wallet. Your wallet contains private keys, used to connect to the Bitcoin network. Unless somebody links your identity with a wallet address you used, your Bitcoin transactions will be anonymous. For example, if you’re buying BTC with your credit card, a data breach can reveal your identity. Online exchanges that offer you to link a credit card with your account, while offering you to use their online wallets at the same time have suffered data breaches in the past.
Advice: As a general rule, it's best not to keep any significant amount of BTC in an online wallet.
Hardware wallet purses offer a better solution for safekeeping your BTC. Hardware wallets are devices that store your private keys offline. They are secure from malware attacks because they are disconnected most of the time. And, the top hardware wallet purses also have extra layers of security. For example, you need to enter a pin code to access the wallet. If you are looking to store a substantial amount of crypto on your hardware wallet, then your best choice is either Ledger Nano X or Trezor Model T.
Advice: Purchase some Bitcoins and then use it to purchase some additional services on the internet. Bitcoin is now widely accepted and you can use it to purchase most items on this list e.g. VPNs, Backup, Routers, etc.
COMPARISON
Use Coin Cards and BitRefill
Even though Bitcoin and other cryptocurrencies have been around for a while, they are still not as easy to use daily as money is. Getting the BTC or other crypto and safekeeping it is far ahead of opportunities to spend. While many merchants are accepting BTC as a payment method, you’ll rarely find a major merchant who accepts other cryptos. BitRefill makes it possible to buy a range of gift cards and mobile refills using six cryptocurrencies.

Aside from that, BTC transactions can take more than 10 minutes to process, and come with a fee. The Bitcoin network fees are currently below $1 but can fluctuate depending on a volume of trading, as do the processing times.
There are several solutions to these issues, both in the development and in use currently. Coin Cards or crypto debit cards enable you to fund a regular debit card with crypto.
Warning: But, when you spend your crypto, you also have to keep in mind the data trail you are leaving behind. You don't need to register to shop on BitRefill, but a debit card provider will ask you to register for an account.
On the other hand BitPay will provide you with a BitPay Prepaid Mastercard which you can use anywhere. Unfortunately it does require a selfie and a government issued document to confirm your identity. Therefore it’s more widely useable but removes the element of privacy.
Advice: Try out BitRefill and BitPay. These services make it easier to use and spend your cryptocurrency.
Use Disposable Credit Cards
Another great way to keep some anonymity and help keep control of your financials is to use disposable credit/ debit cards. These are also known as Prepaid Debit cards. As the name suggests these are intended for single use or for services where you don’t want to use your real card details.

They are especially useful when you’re signing up for services where there is a monthly charge. By using a Disposable Credit Card, you’ll be able to avoid having to spend money by forgetting to cancel services.
Advice: Purchase a Prepaid Debit Card and change the payment details on all of your monthly charge accounts such as streaming, backups, VPNs.
Chapter 11:
What is data privacy ?
Data Privacy relates to how a piece of personal information, or data, is collected, shared and used.
What is data security ?
Data Security protects your data from being compromise by external attackers and malicious intents.
How to protect my personal information ?
Avoid public Internet connection, especially without using a VPN. Don’t share personal information on social networking sites. Use an antivirus to keep your computer protected against all kind of online threats. Encrypt your electronic devices. Lead trackers away from your identity by setting up a business to make purchases for you. Use Bitcoin at its full potential to keep anonymity and safeguard your wallet.
How does a VPN protect me ?
When you connect to a VPN(virtual private network), you are putting an extra server between yourself and the website you want to go to. This server changes your IP address and encrypts your browsing activity.
Is U2F secure ?
If someone gains access to your public key they have no use of it because it is paired only with the corresponding private key stored on your device.
Why should you encrypt your data ?
Data encryption allows you to securely protect data, such as personally identifiable information (PII), that you don’t want anyone else to have access to.
Can Bitcoin transactions be tracked ?
Unless somebody links your identity with a wallet address you used, your Bitcoin transactions will be anonymous.







