Disclaimer: this article includes links to products for sale on our store.
- Introduction
- What is a YubiKey?
- History of YubiKey and Yubico
- How Does the YubiKey work?
- Is It Better than Other 2FA Methods?
- Best YubiKey for every option
- YubiKey vs Password Generators
- Passwordless, 2FA and MFA
- What Protocols Does it Support?
- YubiKey Supported Apps and Software
- What Happens If I Lose My YubiKey?
- How to Avoid Getting Locked out of Your Accounts
- How to Re-Install YubiKey As Your Preferred Login Method
- Can I Use Two Yubikeys?
- YubiKey Alternatives
- Conclusion
- FAQ
In this post we are going to cover:

Plus more... Read on to learn everything you need to know about which YubiKey you should buy.
Thinking of buying a YubiKey? Not sure which one is best for you?
We’ve got you covered!
In this guide, we talk about each YubiKey model. You’ll find the perfect one for you without spending too much money on a model with features you’ll never use. Unfortunately as great as their product is, their layman clarity is the opposite. You can use our table of contents to jump to a section that’s relevant or useful to you.
Introduction
Having your accounts secure is one of the biggest challenges in 2020. Password leaks are constantly happening and it’s difficult to protect against them.
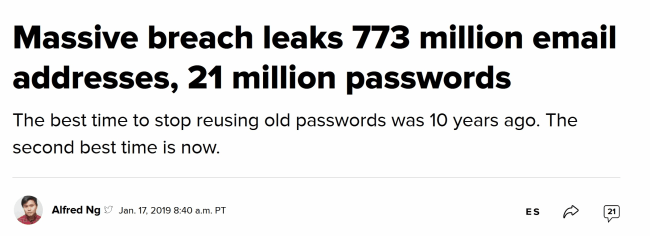
Although the above headline from CNET is from January 2019, you can find more just like it on a near daily bassis.
One of the best ways to protect your privacy is by using a password generator such as LastPass. Unfortunately, even these have their limitations. Hardware based security, such as a YubiKey is nearly impossible to crack. Thus, it can help intensify your data security and safety.
What is a YubiKey?
We’re getting more and more dependent on online platforms for professional and social purposes. This growing trend has increased the need to embrace more reliable online security measures.

One of the most common and reliable ways to protect your accounts is to use two-factor authentication (2FA). The protocol adds an extra layer of security to safeguard your account. Most platforms such as Facebook and Kraken offer 2FA.
When you have this feature enabled, you will have to provide at least two pieces of evidence to get access to your account. The first is usually your password and the second is typically a system-generated code that’s sent to your registered phone or e-mail addresses. You must enter this code before you can get access to your account.
Advice: While this is a popular technique, it is not very safe as anyone may have access to your phone or email. This is why experts now recommend using a piece of hardware to get the job done. One such piece is known as Yubikey.
YubiKey is a compact plastic and metal key that you connect or plug into your device (phone or computer) to authenticate logins. It’s the size of a USB and works just like a physical key to unlock your virtual accounts.
You will find a number of brands offering such keys on the market. They are made according to the Universal 2nd Factor (U2F) standard that marries public key cryptography with hardware-based authentication.
These keys support all major platforms including Windows, MacOS, Facebook, Google, Dropbox, and password managers such as Keepass, Dashlane, and Lastpass.
History of YubiKey and Yubico
The YubiKey is the brainchild of two inventors Jakob Ehrensvärd and his wife Stina Ehrensvärd.
There are many privacy related companies around the world from VPNs to secure backups, password managers, and more. However, Yubico is a company that is truly in a league of its own.
Yubico started out in 2008 in Sweden and aimed to address the password and authentication market in a new way. Now in it’s 5th generation, the YubiKey has undoubtedly achieved its aims.
Info: Unlike other companies, Yubico is completely open-source. Any independent authority can therefore ensure that its product has no back doors, and is completely transparent.
In order to keep moving forward, and have the best talent possible, Yubico also opened offices in Silicon Valley. In total, Yubico invests substantially to provide you with the best hardware authentication, and to keep doing so in the future.
Alongside all of that, Yubico also invests in researching the privacy market. As an example, they publish a yearly state of passwords report.
How Does the YubiKey work?
YubiKey’s genius is hidden in its simplicity. Generally speaking, new security technologies aren’t used by people due to the difficulties they encounter when trying to implement them. Yet, with the YubiKey, the experience is enjoyable.
In fact, setting up different software to use the YubiKey is the most time consuming experience. Fortunately, this is a one-time thing.
To set up a software or app to use the YubiKey the steps are always very similar:
- Go to settings
- Find the two factor authentication options.
- Enable and select YubiKey as an option.
- Plug in your YubiKey and press the button
- That’s it your done
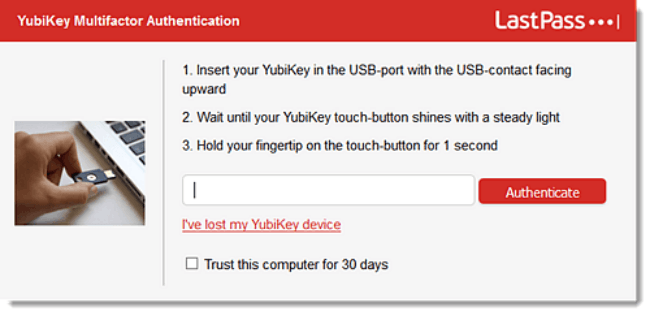
Once set up, using the YubiKey is even simpler. If you’re going passwordless then simply touch the button or hold the YubiKey against your device. If you’re using it for 2FA or MFA it’s the same but you have to enter your password first.
Info: Each key has an increment counter that tells you the number of times you have generated a code with your key. Each Yubikey can handle a specific number of credentials depending on its cost and features.
Only the Yubikey linked to a specific account can be used to gain access to it. Other YubiKeys, even if they are the same type, cannot be used to authenticate accounts. You can, however, add multiple keys to the same account - though usually this requires the original YubiKey to do so. You will have to get in touch with the administrator to add a new YubiKey or temporarily disable 2FA if you lose your key.
Is It Better than Other 2FA Methods?
The YubiKey offers more benefits as it is simpler than using other methods – what will you do if your phone’s out of battery?
It also reduces the risk of breaches since the code can be used only once within a specified period of time. Plus, even if you lose the key, it will not be of risk as it does not contain information such as your passwords or the platforms it is used for.

Moreover, the YubiKey also protects against phishing attacks thanks to the U2F protocol that binds login to the original URL. It will not reveal your credentials if the website is not real. This is very important because about 70% of all cyberattacks use a combination of hacking and phishing techniques.
Best YubiKey for every option
Here are the best YubiKeys to buy right now. In short, it comes down to three simple questions that you should ask yourself:
- What devices do you want to use it with?
- How big would you like it to be?
- How secure do you need it to be?
YubiKey 5 NFC - Best All-Around Option

The YubiKey 5 NFC is hands down the best option on the market right now. It’s USB-A connector allows you to use it with all major computers and laptops. Since it’s not USB-C compatible so you might have some problems with Apple devices. In that case the YubiKey 5Ci is the perfect alternative.
Alongside it’s USB-A connectivity, as the name implies, the YubiKey 5 NFC also has NFC capability. This means you can easily use it with your phone by touching the two together.

The key is smaller than your average house key, and thanks to the useful hole you can add it to your daily keychain. Furthermore, it’s waterproof and crush resistant, meaning you don’t have to worry about driving over it or dropping it down the drain.
The YubiKey comes in packs of 1, 2, 10 or even 50. You get a surprisingly low 4% discount on larger orders. On the whole though, the best YubiKey for most people.
YubiKey 5Ci and 5C - Best For Mac Users

The YubiKey 5Ci is like the 5 NFC, but for Apple fanboys. The majority difference is instead of a USB-A connector it has a USB-C and Lightning connector. Interestingly, this costs close to twice as much as the 5 NFC version.
The 5Ci is the successor to the 5C. It’s a welcome move as the biggest complaint with the 5C is it’s lack of iPhone compatibility.
Similarly to the 5 NFC it’s waterproof and crush proof. If your device ecosystem is more Apple than Windows then the 5Ci will be your best option.
If you only need the USB-C and connector and not the lightning connector, you can save $20 and pickup the Yubikey 5C.

In our opinion, most hardware these days that have a USB-C port also have a USB-A port, and so the YubiKey 5 NFC works fine, and it saves you $5 and has NFC support. Since its just inputting a password, there is no real benefit to using the a USB-C connection over USB-A.
YubiKey 5 Nano - Best For Users with USB-A Connections

The YubiKey 5 Nano is nearly the same as the NFC version but in a small form factor, and the lack of NFC. This makes it perfect if you’d like to use the YubiKey with a single laptop and wouldn’t like it to protrude.
YubiKey 5C Nano - Best For Users with USB-C Connections
The Yubikey 5C Nano is the Apple version of the 5 Nano. It’s a small form factor USB-C YubiKey. Thus, you can conceal it within your laptop and don’t have to worry about constantly plugging and unplugging it. But it does have the downside that if your laptop only has one USB-C port, then it’s not going to be too useful.
Security Key NFC by Yubico - Best For Non-LastPass Users Who Can’t Spend Much

The Security Key NFC is the budget version of the 5 NFC. In most aspects it provides the same functionality and has the same form factor. It’s cheaper because it’s limited in what software it can support. Most importantly, it doesn’t support LastPass. So if you’re planning on getting this version, make sure it supports all the software that you use.
There is also a (very slightly) cheaper non-NFC Security Key, which means you won’t be able to use it on your phone.
YubiKey FIPS Series - Best For Federal Workers and Contractors
The YubiKey FIPS Series enables government agencies and contractors to meet the highest authenticator assurance level from the latest FIPS guidance. Due to the extra requirements it needs to meet, it is more expensive, but nothing too drastic.

The YubiKey FIPS Series is available in all versions that the YubiKey is. Hence you can use our comparison above to decide which one is right for you. You can find all the Yubikey FIPS series keys here.
YubiHSM - Best For Complete Business Security
The YubiHSM is one of the most expensive USB devices we’ve ever seen at a whopping $650! The Yubi Hardware Security Module is aimed at companies aiming for complete privacy and security. It helps companies in the following ways:
- Creating and Storing secure keys
- Extensive cryptographic capabilities
- Secure sessions
- Role-based access control
- Network Shareable
- M of N wrap key Backup and Restore
- Interfaces via YubiHSM KSP, PKCS#11, and native libraries
- Tamper evident Audit Logging
In all honesty, even we don’t understand a majority of the things that the YubiHSM supports. If your company deals with highly restricted or valuable data, then we’d recommend reaching out to Yubico to learn how the HSM can help protect your business.
Info: If you still feel like you aren't sure which YubiKey is best for you, you can always use YubiKey's super detailed comparison page found here. This page is incredibly detailed. There are dozens of factors compared. We think its more confusing than helpful for the average person, but for some who really need to know about specific use-cases, its a good resource.
YubiKey vs Password Generators
With the emergence of tools like Dashlane, 1Password, and LastPass many people have started using stronger passwords. This is definitely a move in the right direction to help protect people’s data. I’ve honest to god had one of my old mayor passwords leaked and tried to be held ransom and it’s a horrendous feeling - even I no longer used the password.

With the YubiKey, it’s impossible for such a thing to happen. Whether you’re using it for passwordless or 2FA, someone would need to know your login details AND have your YubiKey to be able to gain access. With hackers getting smarter by the day, a YubiKey is the only solution to provide true peace of mind.
Passwordless, 2FA and MFA
When it comes to YubiKeys the terms Passwordless, 2FA, and MFA seem to be used interchangeably from site to site. Yet, they aren’t the same thing, and the YubiKey offers all of them.
Passwordless authentication is any type of authentication that doesn’t require a password. With regards to hardware authentication, it can be the pressing of the button that confirms your identity.
2FA is short for two factor authentication. This means that you need two different types of authentication methods before you can log in. Generally speaking, the first one is your password and the second is an SMS or email confirmation code. The YubiKey takes over the latter part.
MFA is short for multi factor authentication. As the name suggests it requires three or more authentication methods before you can log in. This is extremely secure, but of course, time consuming too.

What Protocols Does it Support?
YubiKey supports the following protocols: FIDO & FIDO2, Yubico OTP, OATH HOTP, U2F, PIV, and Open PGP. If you’re like us, those are a random list of letters to you too, so let us break them down for you.
FIDO & FIDO2
FIDO & FIDO2 are authentication methods created by the FIDO Alliance. The FIDO Alliance was created by Yubico to be an independent authority on secure authentication. In short, the alliance aims to develop software and hardware authentication methods that help us reduce our reliance on passwords. As an open-sourced alliance with backing from the majority of silicon valley it’s one of the best and strongest authentication methods around today.
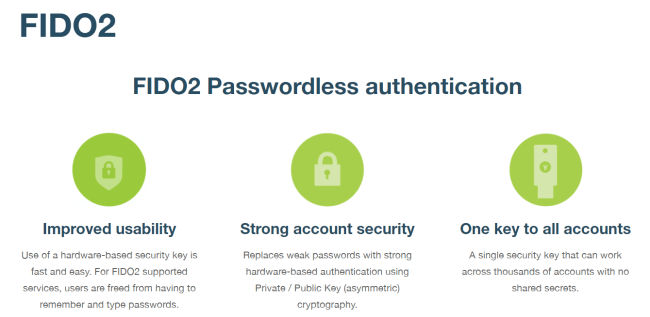
FIDO2 is an evolution of FIDO U2F and offers the same high level of security, with expanded authentication options such as Passwordless, 2FA and MFA.
Yubico OTP
OTP stands for one time passcode. The Yubico OTP works similarly to all other OTP’s that you may get e.g. by phone or SMS when you try to sign-in to your Gmail. To generate a Yubico OTP you just press the button 3 times. The advantage of an OTP is that, as the name suggests, it’s single use. This means that once you’ve used it it’s no longer an active password.
OATH HOTP
OATH (Open Authentication) is an alliance similar to the FIDO alliance. They have two main authentication methods TOTP and HOTP. TOTP is a time-based OTP, however, since the Yubico doesn’t have a built-in clock, it’s not natively supported by Yubico. HOTP is a hash based OTP, and hence it’s supported by YubiKeys.
U2F
U2F (Universal 2 Factor) is a standard that simplifies and strengthens 2FA. Similar to FIDO, it was first developed by Yubico and Google. It’s now owned by the FIDO Alliance to maintain it’s open source standard.
You can see a brief video explaining the concept in more detail below:
PIV
PIV is short for Personal Identity Verification. It’s a Federal Information Processing Standard that is required by all federal employees and contractors in-order to identify themselves.

OpenPGP
OpenPGP is an email encryption protocol that’s less commonly known as Pretty Good Privacy. With the email providers that support it, it helps encrypt email communications to help maintain your privacy.

YubiKey Supported Apps and Software
Thanks to it’s range of authentication methods, YubiKey supports login for 100s of tools and software. Some examples are:
- Unlocking your computer
- Cloud Storage: One-Drive, GDrive, Microsoft
- Social Networks: Facebook, Twitter, Instragram, etc
- Password Managers: LastPass, 1Password, Dashlane
- and so much more
A full list can be found here but for the average person it will support login help for all tools that you use.
Furthermore, due to the openness of the company and the code it’s easy for new companies to integrate FIDO authorization into their login. The harder part is actually convincing a company to add it to their repertoire.
What Happens If I Lose My YubiKey?
YubiKeys have loads of benefits when it comes to enhancing account security. However, these physical devices can quickly get lost due to their small size. Losing a YubiKey can lock you out of your accounts for hours or even days.
Info: The good news is that you can still access your account even after losing your YubiKey. And, yes! It is pretty simple.
You only need to hop into a logged-in device. Then, remove YubiKey as the preferred authentication method.
For instance, if you lose your YubiKey on your way home from work:
- use your home computer or any device still signed in to your account to change the settings
- to access your Google account, just head to ‘My Account,’ then ‘Signing Into Google,’ and select the ‘2 Step Verification’ option
- after pressing the ‘2 step Verification’ button, proceed to click on the pencil icon that is adjacent to the ‘Device name’ button and press ‘remove’
- now you should be able to sign in to your account without entering YubiKey verification
- make sure to set up another email or authentication method to keep your account safe
Alternatively, if you have a backup YubiKey, use it to log into your accounts.
How to Avoid Getting Locked out of Your Accounts
Granted, YubiKeys provide additional online and device safety. They are highly useful when dealing with accounts containing potentially sensitive data.
Advice: However, to safeguard your accounts and avoid being locked out, you have to anticipate the loss of your YubiKey.
Obtain Spare Keys
The safest way is to have a spare key that you can use to access your account in the event of misplacing, losing or damaging the original key. Ideally, keep the spare key separately and in a secure place.

Enable Login Without 2-FA
Advice: In case you don’t have a spare YubiKey, it is advisable to set up at least one device to log in without 2-factor authentication. Doing so will enable you to use the device to remove the two-factor authentication settings in case you lose your YubiKey. Ideally, the device should be your home desktop, laptop, or any other device that you repeatedly use to log in to your accounts.
Enable a Convenient, Alternative Login Method
Google, Facebook, and Dropbox all allow you to set up alternative ways to log in to your accounts. Use this option to select a convenient login method that you can use when you lose or don’t have immediate access to your Yubikey.
How to Re-Install YubiKey As Your Preferred Login Method
You will also be glad to learn that setting up your replacement YubiKey as an authentication method is relatively easy.
Depending on the site or application, proceed to the settings section and click on ‘security’.
You can then proceed to set up the YubiKey as your preferred two-factor authentication method.
Info: If you lose your YubiKey then you can go to your applications and remove its access. Unfortunately, if you have a lot of accounts that you use your YubiKey with, then this can take a fair amount of time.
The most problematic part is that you may lose access to your accounts. By default, most apps and software provide you with a recovery method in case you lose your YubiKey - therefore always make sure that you keep these somewhere secure and accessible.
However, it is possible to duplicate a YubiKey so that if you lose one, you have another one that functions the same.
Info: The only exception to this is the Mac Log-on Tool as that also inspects the serial number of the key which is impossible to duplicate. This doesn't mean you can't have a backup. It just means you need to tell your Mac you have two authorized YubiKeys.
Having a duplicated YubiKey is the best method. Unfortunately, having other recovery options creates a weak point. Anyone wishing to gain access to your account can try the recovery options, thereby bypassing the need for the YubiKey.
Can I Use Two Yubikeys?
Yes, you can use two YubiKeys at once. There are two different methods: duplication and side-by-side. With the former you can “clone” your YubiKey so that you can use them as they were the same e.g. a 5C for your MacBook and a 5 NFC for your phone and desktop PC.

With the latter you can easily use two or more YubiKeys separately. However, this does require you to authenticate each one with your apps. For most apps this won’t be a problem, but some might only allow you to register one YubiKey at a time.
YubiKey Alternatives
Yubico started the hardware security key trend and therefore, it’s no surprise that they are the leader in the industry and almost everyone recommends their products. This isn’t to say that there aren’t some great alternatives out there. In fact, some companies have added some welcome developments such as a Bluetooth support and fingerprint reading.
Thetis Fido U2F with Bluetooth
The Thetis Fido is extremely useful, as it supports a USB-A port and Bluetooth, making it perfect for nearly all devices. At $29.99 it’s extremely affordable, and with its rotating metal cover it’s durable too.

Unfortunately, their Bluetooth version only supports U2F and not FIDO, so you’ll be lacking access to some useful tools such as LastPass. They do sell a FIDO version too but that only supports USB-A so you’ll only be able to use it with some devices. If they would combine Bluetooth and FIDO support, they would come close to beating the YubiKey.
Google Titan Security Key
Since Google helped Yubico develop the FIDO authentication method, it’s not surprising that they have their own security key. The Google Titan Security Key comes in three different flavours: USB-C, USB-A & NFC, and BLuetooth & NFC.

On the whole, they support a great variety of standards but their build quality doesn’t seem to be as high as for the YubiKey.
CryptoTrust OnlyKey
The CryptoTrust OnlyKey supports a whole range of authentication methods including FIDO2 / U2F, Yubico OTP, TOTP, and Challenge-response. The OnlyKey is special in the fact that it has a PIN pad that helps you against keyloggers and adds an additional layer of security to your passwords. Furthermore, after 10 incorrect tries, the device will wipe itself to prevent intruders.

While it might not look it, it’s also waterproof and very durable. If it wasn’t for only the USB-A support this would likely take the number two spot.
Qkey Smartkey
The Qkey Smartkey is intended to be a superpowered personal protection device with a whole range of features including a proximity sensor. Unfortunately it’s only USB-A and many of the features that they propose are still under development.

Kensington VeriMark
The Kensington VeriMark is a fingerprint enabled hardware security device. As they have been producing USB drives and fingerprint readers for years, the quality of the device can be highly trusted. As with all of the other YubiKey alternatives, it supports a whole range of authentication including FIDO. Overall it’s a great product, but again it’s restricted by the USB-A only support, and we think the fingerprint sensor is overkill for the average person.

Conclusion
YubiKeys are used by some major companies around the world including Google. According to reports, the company has been using YubiKeys since 2009.
The company turned to YubiKeys after suffering a major data breach in 2009. It joined hands with Yubico to increase the capabilities of the system by including public key cryptography. This gave us the U2F protocol, mentioned earlier.
Google has now integrated support for the YubiKey into security protections for all its users. It has been proven to be secure and reliable.
You will find many models of the key on the market including a version that’s meant to kill passwords. However, no consumer services are currently willing to support passwordless login. Nonetheless, many experts believe that this is the beginning of a passwordless era.
YubiKey is a hardware security device to help you access accounts with ease and security. Hardware keys are more secure than passwords as they can’t be spoofed or copied. At they same time, they are easier to use than traditional 2 factor apps.
Simply put, a YubiKey will help simplify logins. Whereas, generally speaking, Google, Apple, your bank, etc might send you a login code by email or text, with a YubiKey you simply plug it in and press it when 2FA is required.
This means you no longer need to rely on apps like Google atuhenticator which have lots of security issues.
On the whole, YubiKeys are fantastic devices and it’s by far the best investment you can have in your online privacy and security. The YubiKey 5 NFC will suit most people and we’d highly recommend you getting one.
FAQ
Do I Need a YubiKey?
Unless you work for the government or a large company with trade secrets, you likely do not NEED a YubiKey. However, it is highly encouraged that everyday users secure their accounts with a hardware 2nd factor when possible.
How Much Does YubiKey cost?
Prices for YubiKeys vary based on supported connections and levels of encryption. The cheapest YubiKey (the ‘security key’) runs $20, but you can spend up to $650 for their most secure product (the ‘YubiHSM’).
What if I lose my YubiKey?
If you lose your YubiKey, there is generally not too much to worry about as long as there is no easy way for someone to tie that YubiKey to you and you use strong passwords for your accounts. The big issues is getting back into your accounts without it. This is why it is advised to have more than YubiKey set up on your accounts so that you always have a backup. Use the backup to get back into your accounts and delete the missing YubiKey as an authorized second factor.
Can I Use YubiKey with iPhone?
Any YubiKey with ‘NFC’ in the name will allow you to use it with any iPhone 6 or later.
How Safe is YubiKey?
Any YubiKey is incredibly safe for the average user. Those who need additional security can purchase a FIPS series Yubikey or a YubiHSM product for even more impressive levels of security.
Does YubiKey wwork with Amazon?
Unfortunately, Amazon does not support the use of hardware second factors like YubiKey. Amazon’s only supported form of of two factor is SMS messages via your mobile phone.
Is YubiKey Safe?
YubiKey is as safe as you can get when it comes to protecting your online privacy. It’s the safest method out there.
What is a hardware security key?
As we mentioned, YubiKey is a hardware security key. What this means is that you physically need to own it in order to be able log in to your accounts. Simply put it works through cryptography and it’s impossible to fool).



